How To Use Safe Mode To Remove Malware
How to use safe mode to remove malware is crucial for computer security. Safe mode provides a controlled environment to tackle malicious software, minimizing disruption and potential damage. This guide will walk you through the entire process, from understanding safe mode to post-removal checks, ensuring a clean and secure system.
This comprehensive guide covers entering safe mode across various operating systems, identifying malware’s telltale signs in safe mode, and removing malware effectively using safe mode tools and techniques. It also includes troubleshooting common issues and preventative measures to avoid future infections.
Understanding Safe Mode
Safe mode is a troubleshooting feature in many operating systems, providing a limited environment for diagnosing and resolving issues. It allows users to identify and address problems without the complexity of a fully functional operating system. This mode is particularly useful for tackling malware infections, hardware conflicts, or software malfunctions.Safe mode operates with a drastically reduced set of drivers and services, simplifying the operating system’s configuration and often isolating the source of a problem.
This limited environment can be invaluable for isolating the source of problems and for resolving them more effectively.
Safe Mode Operation
Safe mode differs significantly from normal mode operation. In normal mode, the operating system loads a comprehensive set of drivers and services, enabling a full range of hardware and software functionalities. This full configuration is optimal for everyday tasks but can make it harder to identify problems, particularly those related to software or hardware conflicts. In contrast, safe mode loads only the essential drivers and services, minimizing the potential for conflicts.
Key Differences Between Normal and Safe Mode, How to use safe mode to remove malware
The following table Artikels the key differences between normal mode and safe mode operation:
| Feature | Normal Mode | Safe Mode |
|---|---|---|
| Drivers Loaded | Full Driver Set | Limited Driver Set |
| Services Running | All Services | Essential Services Only |
| Performance | Higher | Lower |
| Susceptibility to Malware | Higher | Lower (in theory) |
Reasons for Using Safe Mode
Safe mode is often employed when users encounter problems that interfere with normal operation. Common reasons for booting into safe mode include suspecting malware infections, troubleshooting unusual system behavior, or resolving conflicts with recently installed hardware or software. Safe mode provides a controlled environment to address these issues. By loading a minimal set of drivers and services, safe mode can isolate the source of the problem, allowing for a focused approach to resolution.
For instance, a user experiencing erratic mouse behavior might boot into safe mode to determine if the issue stems from a specific driver or if a more systemic problem is present.
Entering Safe Mode
Safe mode is a diagnostic mode that boots your computer with a minimal set of drivers and programs. This allows you to isolate potential issues with software or hardware that might be interfering with normal operation. It’s a valuable tool for troubleshooting and resolving problems.This section details how to enter safe mode on various operating systems, highlighting the differences in methods and options.
Understanding the process for entering safe mode is crucial for effectively addressing system malfunctions and ensuring your computer operates smoothly.
Entering Safe Mode on Windows
Windows offers several variations of safe mode, each with a slightly different configuration. These variations allow for isolating specific software or hardware conflicts.
- Safe Mode: This is the most basic safe mode, loading only essential drivers and programs. It’s suitable for troubleshooting issues related to corrupted or interfering software.
- Safe Mode with Networking: This option is identical to safe mode but includes network drivers, enabling internet access. This is useful for updating drivers or accessing online troubleshooting resources.
- Safe Mode with Command Prompt: This loads safe mode with the command prompt, offering advanced troubleshooting options through text-based commands. This mode is for users comfortable with command-line interfaces.
- Safe Mode with Graphical User Interface: This mode loads a graphical user interface (GUI), making it easier for users unfamiliar with command prompts to interact with the system. It allows for the same diagnostics and troubleshooting options as basic safe mode.
Entering Safe Mode on Windows 11
To enter safe mode on Windows 11, follow these steps:
- Shut down your computer completely.
- Turn your computer back on.
- Repeatedly press the F8 key during the boot-up process. The exact timing is crucial; you need to press F8immediately* after seeing the initial startup screen. This will bring up the advanced boot options menu.
- Use the arrow keys to highlight “Safe Mode” and press Enter.
- Your computer will now boot into safe mode.
Entering Safe Mode on macOS
macOS uses a different approach to safe mode, leveraging system preferences and restart options. Safe mode in macOS is not as varied as in Windows.
- Click the Apple menu in the top-left corner of the screen.
- Select “Restart.”
- During the restart process, hold down the Shift key.
- Your computer will boot into safe mode.
Safe Mode Boot Options Comparison
The following table summarizes the different safe mode options across operating systems:
| Operating System | Safe Mode Types | Description |
|---|---|---|
| Windows | Safe Mode, Safe Mode with Networking, Safe Mode with Command Prompt, Safe Mode with Graphical User Interface | Offers various options for different troubleshooting scenarios. |
| macOS | Safe Mode | Simple approach, focusing on a single mode. |
Identifying Malware in Safe Mode
Malware often behaves differently in safe mode, providing crucial clues for identification. This distinct behavior arises from the limited services and applications running in safe mode, allowing a clearer view of system processes and resource usage. Recognizing these variations is vital for accurately pinpointing malicious activity.Safe mode offers a controlled environment to observe system performance and identify unusual activity that might indicate malware.
By isolating the potential source of issues, users can more effectively determine the nature and extent of the threat. This, in turn, enables more targeted and effective remediation strategies.
Malware Manifestation Differences in Safe Mode
Safe mode significantly restricts background processes, which can mask the effects of malware. Consequently, malware symptoms that are prominent in normal mode might be less noticeable or even disappear entirely in safe mode. This difference is crucial for diagnosis. For example, a program consuming significant system resources in normal mode might exhibit minimal or no resource consumption in safe mode.
A program that exhibits high disk activity in normal mode may show little or no activity in safe mode.
Indicators of Malware Presence in Safe Mode
Several indicators can point towards the presence of malware in safe mode. Careful observation of system behavior, particularly regarding performance and resource usage, is key. Look for any anomalies that suggest malicious activity.
Common Malware Symptoms to Watch For in Safe Mode
A range of symptoms can signal malware, even in safe mode. These symptoms might be less pronounced than in normal mode but can still be detectable.
- Reduced system responsiveness. A system that is normally responsive might become sluggish or unresponsive in safe mode.
- Unusual or excessive hard drive activity. This could manifest as unusually high read or write speeds.
- Unexpected or unexplained network activity. This includes unusual network connections or communication patterns.
- New or unfamiliar processes running. Look for processes that weren’t present in previous safe mode sessions.
- Unusual system startup or shutdown behavior. Pay close attention to any changes in the system’s startup or shutdown procedures.
Importance of Observing System Behavior in Safe Mode
Observing system behavior in safe mode is paramount for accurate malware detection. The limited environment of safe mode provides a clearer view of the system’s core functions, allowing users to isolate potential problems and pinpoint malicious activities. This helps differentiate between legitimate system processes and those that might be malicious.
Comparing System Performance in Safe Mode and Normal Mode
Comparing system performance between safe mode and normal mode is a valuable diagnostic tool. This comparison can reveal significant anomalies indicative of malware. A significant performance difference between the two modes can point towards malicious activities that are masked in normal mode.
Table of Common Malware Behaviors and Safe Mode Manifestations
The table below summarizes how common malware behaviors might manifest differently in safe mode.
| Malware Behavior | Safe Mode Manifestation |
|---|---|
| High CPU Usage | Reduced or negligible CPU usage |
| High Disk Activity | Reduced or negligible disk activity |
| Unusual Network Activity | Reduced or negligible network activity |
| Unidentified Processes | Absence of unfamiliar processes |
Removing Malware in Safe Mode
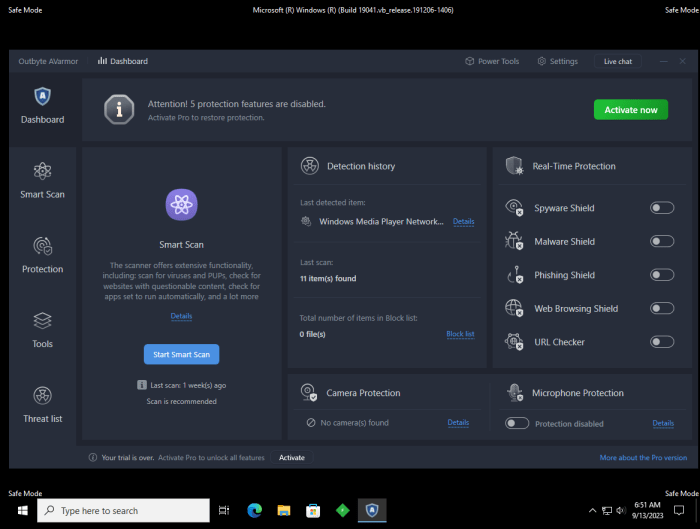
Source: softwaretested.com
Safe mode provides a restricted environment to tackle malware, minimizing potential interference with crucial system processes. This environment allows for targeted malware removal without the complications of running applications and services that could be compromised. Careful execution of removal procedures in safe mode is crucial for a successful remediation.Effective malware removal in safe mode hinges on methodical steps and the appropriate tools.
Antivirus software, system restore, and dedicated removal tools are crucial components in this process. Understanding how to utilize each tool effectively is key to a successful outcome.
Malware Removal Tools in Safe Mode
Various tools are available for malware removal in safe mode. A robust antivirus program, often the first line of defense, is essential. Specialized malware removal tools, often provided by security vendors or independent security researchers, can be valuable for handling specific threats. These tools are usually designed for in-depth scans and removal of malicious components.
- Antivirus Software: A reputable antivirus program with up-to-date definitions is critical for detecting and removing malware. It should be capable of running full system scans even in safe mode. Examples include: Norton, McAfee, Bitdefender, and others.
- Specialized Malware Removal Tools: Some malware may require specialized tools for complete removal. These tools can target specific types of malware and have more advanced techniques for eliminating them. Examples include Malwarebytes and other dedicated malware removal utilities.
Using Antivirus Software Effectively in Safe Mode
Antivirus software is a powerful tool for malware detection and removal. Using it in safe mode ensures that the antivirus program has full control of the system, free from potential conflicts with other programs. It’s important to run a full system scan in safe mode.
- Open the antivirus software. The exact steps vary depending on the specific program. Locate the scan options.
- Select “Full Scan” or a similar option. This ensures thorough examination of all system files and folders.
- Allow the scan to complete. This may take some time, depending on the size of the hard drive and the complexity of the scan.
- If malware is detected, follow the instructions provided by the antivirus program to remove it. Be cautious and follow the prompts meticulously.
Using System Restore to Revert to a Previous State
System restore allows reverting the system to a previous point in time. This is useful if malware infection occurred recently and a system backup was not created. Restoring to a previous state can sometimes be the fastest way to return the system to a known good state.
- Access the System Restore utility. This is usually located within the system settings or recovery options.
- Select a restore point. Carefully examine the available restore points to ensure you are selecting a point before the malware infection.
- Follow the on-screen instructions to initiate the restore process. This process typically involves confirming the selected restore point.
Running a Full System Scan with Antivirus Software in Safe Mode
This step-by-step guide Artikels running a full system scan with Norton Antivirus in safe mode. This procedure can be adapted for other antivirus software.
- Boot into Safe Mode. This is done by restarting the computer and pressing a specific key combination, such as F8 or Shift+F8.
- Open Norton Antivirus. Locate the program icon and launch it.
- Initiate a full system scan. Navigate to the scan options and select “Full Scan.”
- Allow the scan to complete. The scan will identify and quarantine any threats detected.
- Follow the on-screen instructions to remove any detected malware.
Potential Limitations and Considerations
Safe mode offers a controlled environment but may have limitations. Some malware may have already modified system files, making complete restoration challenging. Furthermore, restoring to an earlier point might lose some recently saved files. Care should be taken when considering a system restore.
Methods for Safely Removing Malware
A combination of methods often yields the best results. First, try running a full system scan with a reputable antivirus program. If the infection is persistent, consider specialized malware removal tools. System restore is another potential solution, especially if the malware infection is recent.
Post-Removal Checks and Precautions
Successfully removing malware from your system is a crucial step, but it’s not the end of the process. Thorough post-removal checks and preventative measures are essential to ensure the infection doesn’t return and to maintain a secure system. This section details how to verify complete removal, implement preventative scans, and strengthen your system’s defenses.
Verifying Complete Malware Removal
Post-removal verification is vital to confirm that the malware is completely eradicated from your system. Simply running a scan after the removal process isn’t sufficient; you must meticulously review the results. This involves checking for remnants of the malware in hidden folders, registry entries, and startup processes. Failure to do this could leave the system vulnerable to re-infection.
Running a Post-Removal Scan
Running a comprehensive post-removal scan is critical. This step ensures that no traces of the malware remain, preventing potential future issues. Employing reputable anti-malware tools is key. These tools can detect hidden files and processes that might have evaded the initial removal process. Look for indicators like unusual processes, system slowdown, or changes in file sizes or permissions.
Preventing Malware Return
Preventing a return of malware requires a multi-faceted approach. Proactive measures are paramount to safeguarding your system. This involves creating a list of preventative measures.
- Regular System Scans: Schedule regular scans with your anti-malware software to identify and eliminate threats as they arise. This proactive measure is essential to maintaining a secure system.
- Update Software Regularly: Keeping your operating system and applications updated is critical. Updates often include security patches that address vulnerabilities exploited by malware. This proactive measure ensures your system has the latest protection.
- Enable Real-Time Protection: Enabling real-time protection in your anti-malware software is crucial. This feature actively monitors your system for suspicious activity and blocks potential threats in real-time. This continuous monitoring is essential to maintaining a secure environment.
- Use Strong Passwords: Employing strong, unique passwords for all your accounts is a fundamental security practice. Strong passwords help prevent unauthorized access to your system and data. This proactive measure safeguards your accounts and data.
- Avoid Suspicious Links and Downloads: Exercise caution when clicking on links or downloading files from unknown sources. Malicious links and downloads are common infection vectors. This proactive measure prevents unwanted infections.
- Enable Firewall Protection: Employing a robust firewall to monitor and control network traffic is essential. A firewall acts as a barrier between your system and the internet, blocking unauthorized access. This proactive measure protects your system from network-based threats.
Strengthening System Defenses
Strengthening system defenses involves implementing a layered approach to security. This multifaceted strategy encompasses multiple aspects of your system configuration and user behavior. It is crucial to incorporate several measures to fortify your system against future attacks.
- Install a reputable firewall: A firewall acts as a barrier between your system and the internet, preventing unauthorized access. This proactive measure prevents network-based threats.
- Use a robust antivirus and anti-malware suite: A strong suite of security tools is crucial. These tools actively monitor your system and identify potential threats. Employing these tools is essential to safeguarding your system from a variety of malware.
- Enable automatic updates for all software: Keeping software updated ensures you have the latest security patches to address known vulnerabilities. This proactive measure strengthens your system against future attacks.
- Educate yourself about common malware types and their methods of infection: Understanding how malware operates helps you identify and avoid potential threats. Knowledge is a powerful tool in preventing malware infection.
- Avoid clicking on suspicious links or attachments: Exercise caution when interacting with unfamiliar links or files. This proactive measure is a fundamental aspect of safeguarding your system.
Regular Security Updates and Maintenance
Regular security updates and software maintenance are critical for maintaining a secure system. These updates often include crucial security patches that address vulnerabilities, preventing potential exploits. This ongoing maintenance is vital to protecting your system. It helps to prevent malware from gaining access to your system.
Troubleshooting Safe Mode Issues: How To Use Safe Mode To Remove Malware
Safe mode, while a valuable tool for malware removal, can sometimes present challenges. This section details common problems encountered during safe mode entry and execution, along with solutions and diagnostic procedures. Understanding these issues will help you navigate potential roadblocks and successfully complete the malware removal process.
Common Safe Mode Entry Problems
Often, the difficulty in accessing safe mode stems from configuration or hardware issues. These problems can be resolved by systematically checking and adjusting various settings.
- Incorrect Boot Sequence: Ensure your computer’s BIOS settings are configured to allow safe mode boot options. Sometimes, these options are hidden or require specific key combinations during boot-up. Refer to your computer’s manual for specific instructions on enabling safe mode options in the BIOS.
- Hardware Conflicts: Issues with hardware components, such as a malfunctioning hard drive or RAM, can prevent safe mode from loading correctly. If you suspect a hardware problem, check for any error messages during boot-up or try booting with different RAM sticks to rule out compatibility issues.
- Operating System Errors: Corrupted or damaged system files within the operating system can also cause difficulties in entering safe mode. Running system file checks or using recovery tools might help restore the necessary files.
Diagnosing Safe Mode Boot Issues
Troubleshooting safe mode boot problems often involves a systematic approach to pinpoint the source of the issue. Begin by checking the most likely causes and then proceed to more complex diagnostics.
- Boot Errors: Pay close attention to any error messages displayed during the boot process. These messages often contain clues about the cause of the problem. Note the specific error message for further research and troubleshooting.
- Checking Boot Sequence: Verify that the computer’s boot order is set correctly in the BIOS. The correct boot order ensures that the operating system is properly recognized and loads correctly. Incorrect boot order can lead to the operating system not loading.
- System File Integrity Checks: If you suspect corrupted system files, run built-in system file integrity checks or use dedicated system repair tools. These tools can help identify and repair corrupted files, which might resolve safe mode boot issues.
Potential Causes of Safe Mode Failure
Several factors can lead to safe mode failing to load. These range from minor configuration errors to more significant hardware or software problems.
- Driver Conflicts: Incompatible or corrupt device drivers can interfere with safe mode loading. Updating or reinstalling drivers for problematic devices might resolve the issue.
- Third-Party Software Conflicts: Occasionally, third-party software or applications can conflict with safe mode. Temporarily disabling or uninstalling recently installed software may help.
- Boot Sector Corruption: A corrupted boot sector can prevent the operating system from loading correctly, including safe mode. Using recovery tools or reinstalling the operating system might be necessary to resolve this.
Troubleshooting Safe Mode Loading Failure
If safe mode fails to load, follow these steps to pinpoint the problem. These steps cover a range of potential issues and provide solutions to address them.
- Restarting the Computer: Sometimes, a simple restart can resolve temporary glitches that prevent safe mode from loading. Restarting the computer often clears minor memory issues.
- Using Safe Mode with Networking: If possible, try booting into safe mode with networking enabled. This allows access to online resources and support tools to assist in troubleshooting.
- Using System Recovery Options: In some cases, safe mode may not load, but recovery options might. Explore the available recovery options if safe mode fails to load.
Specific Errors and Solutions
Several error messages can occur during safe mode loading. Understanding these errors and their associated solutions is crucial for successful troubleshooting.
| Error Message | Possible Solutions |
|---|---|
| “Boot Device Not Found” | Check the boot order in BIOS settings, ensure the boot device is properly connected, and check for any physical damage to the drive. |
| “Operating System Not Found” | Verify the operating system installation and check for disk errors using disk management tools. Reinstalling the operating system might be necessary. |
| “File System Error” | Run disk repair tools to check and fix file system errors. Reinstalling the operating system may be necessary for severe corruption. |
Closing Summary
In summary, using safe mode is a powerful tool for malware removal. By understanding safe mode’s limitations and utilizing the appropriate tools, you can effectively tackle infections and restore your system to a healthy state. Remember to always back up your data before proceeding with any malware removal steps. Regular security practices and updates will further fortify your system against future threats.












Post Comment