Crud App Tutorial Php Mysql
CRUD app tutorial PHP MySQL walks you through crafting dynamic web applications. This comprehensive guide explores the core concepts of Create, Read, Update, and Delete operations, using PHP and MySQL. We’ll delve into the intricate details of database interactions, secure coding practices, and user interface design. Learn to build robust, interactive web applications with this in-depth tutorial.
The tutorial covers essential steps from setting up your development environment to implementing security measures and error handling. You’ll learn how to effectively use PHP to communicate with MySQL databases, ensuring data integrity and user experience. Expect detailed code examples and practical applications throughout the guide, allowing you to develop and deploy your own CRUD apps.
Introduction to CRUD Operations
CRUD operations, an acronym for Create, Read, Update, and Delete, form the bedrock of data management in web applications. They represent the fundamental actions performed on data within a database. These operations are essential for building dynamic websites and web applications that interact with user input and data storage.A CRUD application, at its core, is a system designed to manage data efficiently.
This includes allowing users to interact with the data, whether adding new information, retrieving existing data, modifying existing records, or removing unwanted entries. The power of CRUD lies in its ability to handle the full lifecycle of data within a system.
CRUD Operations Explained
CRUD operations are the core functions of any database-driven application. Create allows for the addition of new data. Read enables retrieval of existing data. Update facilitates modification of existing data. Delete allows removal of data from the database.
These four operations together encompass the complete process of data management.
Significance of CRUD Apps in Web Development
CRUD applications are crucial in modern web development because they form the foundation for interactive web applications. They enable dynamic data interaction, allowing users to input, retrieve, modify, and delete data within the application. This dynamic interaction is the cornerstone of modern web applications, and the ability to perform CRUD operations is essential for creating truly interactive and useful web applications.
General Architecture of a CRUD Application
A typical CRUD application has a three-tier architecture: the presentation layer, the application layer, and the data layer. The presentation layer, typically built using HTML, CSS, and JavaScript, handles user interaction and displays data. The application layer, built using programming languages like PHP, processes user requests, validates input, and interacts with the data layer. The data layer, which utilizes databases like MySQL, stores and retrieves data.
This separation of concerns allows for scalability, maintainability, and better organization of the application.
Roles of PHP and MySQL in a CRUD Application
PHP acts as the intermediary between the user interface and the database. It handles user requests, validates input, and constructs SQL queries to interact with the MySQL database. MySQL, on the other hand, serves as the persistent data store. It stores the data and executes the SQL queries sent by PHP. PHP receives the results from MySQL and formats them to be displayed to the user.
Data Flow Diagram
A simple diagram illustrating the data flow between PHP and MySQL in a CRUD application is as follows:
+-----------------+ +-----------------+
| User Interface |-----| PHP |
+-----------------+ +-----------------+
| (HTML, JS) | | (Application) |
| Input/Output | | Validation |
| | | SQL Query |
+-----------------+ +-----------------+
^ |
| v
| +-----------------+
| | MySQL DB |
| +-----------------+
| (Data Storage) |
| |
| |
| |
+-----------------+
The diagram shows the user interacting with the application layer, which in turn communicates with the data layer (MySQL).
PHP receives and processes the results from the database, then outputs data to the user interface.
Setting up the Development Environment
Getting your development environment ready is crucial for building your CRUD application. This involves installing the necessary software, configuring them, and creating the database structure. Proper setup ensures smooth execution and prevents potential errors.
A well-structured environment streamlines the development process, allowing you to focus on building the application logic rather than troubleshooting technical issues. The following steps detail the essential setup.
Installing PHP
To develop a PHP CRUD application, you’ll need a PHP interpreter. Different operating systems have varying installation procedures. For Linux distributions, packages are often available through your system’s package manager (e.g., apt-get, yum). On Windows, you can use XAMPP or WAMP, which bundle Apache, MySQL, and PHP. For macOS, you can install PHP using Homebrew.
Verify PHP installation by running `php -v` in your terminal.
Installing MySQL
MySQL is the database management system used for storing data in your CRUD application. Installation procedures vary based on your operating system. On Linux, use package managers like apt-get or yum. On Windows, use installers from official sites or bundled applications like XAMPP. For macOS, use Homebrew.
Once installed, you’ll need to configure MySQL, including setting up a root password.
Setting up the Database
A database is essential for storing and retrieving data. A new database needs to be created for your CRUD application. The `CREATE DATABASE` command in MySQL is used for this purpose. For example, to create a database named `crud_db`, use the command `CREATE DATABASE crud_db;`. You’ll also need to create a user with appropriate privileges to access the database.
After creating the database, you can connect to it using the MySQL client.
Creating the Table Structure
The table structure defines the layout of the data within the database. This includes defining columns, data types, and constraints. A table `users` with columns for `id`, `username`, `password`, `email` can be created using the `CREATE TABLE` command. An example is shown below:
“`sql
CREATE TABLE users (
id INT PRIMARY KEY AUTO_INCREMENT,
username VARCHAR(255) NOT NULL,
password VARCHAR(255) NOT NULL,
email VARCHAR(255) UNIQUE
);
“`
A table for `products` could have columns for `id`, `name`, `description`, `price`. The structure should be tailored to your specific application needs.
Choosing PHP Libraries/Frameworks (Optional)
While not strictly necessary, PHP frameworks like Laravel or Symfony can streamline development and offer pre-built components for common tasks. Laravel’s elegant structure and extensive features make it a powerful choice for building complex applications. Symfony is another widely used framework known for its flexibility and extensibility. Choosing a framework depends on the complexity of your project.
Creating Data Records (Create)
Inserting new data into a MySQL database is a crucial aspect of any CRUD application. This section details the process, emphasizing secure coding practices and robust error handling. Proper implementation ensures data integrity and prevents potential vulnerabilities.
PHP provides robust methods for interacting with MySQL databases. A key element is using prepared statements to safeguard against SQL injection attacks. This proactive measure strengthens the application’s security posture.
Interacting with MySQL for Data Insertion
PHP’s MySQLi extension or PDO offer methods to execute SQL queries. The `mysqli_query` function (or PDO’s `prepare` and `execute` methods) is fundamental for data insertion. The following illustrates the core steps.
Using Prepared Statements
Prepared statements are a cornerstone of secure database interactions. They effectively separate the query structure from the data values. This separation mitigates the risk of SQL injection vulnerabilities, where malicious input can manipulate the query’s logic.
Prepared statements prevent attackers from injecting malicious SQL code into the query, enhancing application security.
PHP Code Examples for Data Insertion
The following example demonstrates inserting data into a “users” table with columns “username”, “email”, and “password”. It employs prepared statements for security.
“`PHP
connect_error)
die(“Connection failed: ” . $conn->connect_error);
// Example data (replace with user input)
$username = “newuser”;
$email = “newuser@example.com”;
$password = “securepassword”;
// SQL query using prepared statements
$stmt = $conn->prepare(“INSERT INTO users (username, email, password) VALUES (?, ?, ?)”);
// Bind parameters (crucial for security)
$stmt->bind_param(“sss”, $username, $email, $password);
// Execute the statement
if ($stmt->execute())
echo “New record created successfully”;
else
echo “Error: ” . $stmt->error;
// Close statement and connection
$stmt->close();
$conn->close();
?>
“`
Handling User Input Validation
User input should always be validated before being used in SQL queries. This prevents unexpected data that could compromise the application.
- Data Type Validation: Ensure input matches expected types (e.g., email addresses, integers). This helps prevent invalid data from entering the database.
- Length Validation: Restrict input lengths to prevent exceeding column limits, ensuring data integrity and preventing potential errors.
- Sanitization: Remove potentially harmful characters from user input using functions like `mysqli_real_escape_string` (or PDO’s equivalent) to prevent SQL injection vulnerabilities.
Best Practices for Error Handling
Robust error handling is critical during data insertion. It allows for graceful failure and prevents unexpected behavior.
- Connection Errors: Check for database connection errors using `$conn->connect_error` to prevent application crashes.
- Query Errors: Check the result of `$stmt->execute()` to catch errors during query execution. Examine the `$stmt->error` for specific issues.
- Input Validation Errors: Handle situations where validation fails, providing informative messages to users and preventing unexpected database interactions.
Retrieving Data Records (Read)
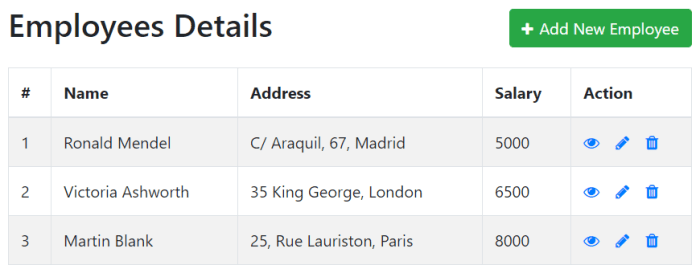
Source: tutorialrepublic.com
Retrieving data from a MySQL database is a crucial part of any web application. This process, often referred to as the “Read” operation in CRUD, allows users to view and interact with the stored information. Efficient data retrieval is essential for providing a responsive and user-friendly experience.
Retrieving data involves executing SQL queries to fetch records from a database table. PHP plays a vital role in connecting to the database and processing the results. The retrieved data can then be displayed in various formats, such as tables or lists, making it easily understandable and usable.
Fetching Data from the Database
To fetch data, a PHP script establishes a connection to the MySQL database using the mysqli extension. This involves providing the database credentials (host, username, password, database name). The script then executes a SELECT query to retrieve the desired data.
“`PHP
connect_error)
die(“Connection failed: ” . $conn->connect_error);
$sql = “SELECT
– FROM yourtable”;
$result = $conn->query($sql);
if ($result->num_rows > 0)
// output data of each row
while($row = $result->fetch_assoc())
echo “id: ” . $row[“id”]. ”
-Name: ” . $row[“name”]. ”
“;
else
echo “0 results”;
$conn->close();
?>
“`
This code example connects to a database, executes a query to select all rows from a table named “yourtable”, and then iterates through each row, printing the values of the ‘id’ and ‘name’ columns. Adapt the table and column names to match your specific database structure.
Using Loops and Arrays to Display Data
After retrieving data, it’s often necessary to organize and present it in a user-friendly format. PHP arrays are ideal for this purpose. The `fetch_assoc()` method retrieves each row as an associative array, allowing access to specific columns using their names.
“`PHP
while($row = $result->fetch_assoc())
$data[] = $row; // Store each row in an array
// Display data in a table format
echo ”
| ID | Name |
|---|---|
| ” . $row[“id”] . “ | ” . $row[“name”] . “ |
“;
“`
This refined example stores each row in an array called `$data` and then iterates through it to create a formatted table, enhancing the presentation of the retrieved data.
Paginating Results for Large Datasets
For large datasets, displaying all records at once can be inefficient and slow. Pagination divides the data into smaller pages, improving performance and user experience. A simple pagination system involves calculating the start and end points for each page.
“`PHP
// Calculate offset for pagination
$page = isset($_GET[‘page’]) ? $_GET[‘page’] : 1;
$perPage = 10; // Number of records per page
$offset = ($page – 1)
– $perPage;
$sql = “SELECT
– FROM yourtable LIMIT $offset, $perPage”; // Modify query to include pagination
“`
Adjusting the `LIMIT` clause in the SQL query allows you to fetch only the desired portion of data for a specific page. This ensures only the necessary data is retrieved and displayed.
Filtering and Sorting Data
SQL queries can be further customized to filter and sort data based on specific criteria. Filtering allows you to narrow down the results, and sorting ensures the data is displayed in a specific order.
“`PHP
$sql = “SELECT
– FROM yourtable WHERE category = ‘books’ ORDER BY name ASC”;
“`
This query retrieves all records from the “yourtable” where the ‘category’ is ‘books’ and sorts them alphabetically in ascending order based on the ‘name’ column. Adjust the `WHERE` and `ORDER BY` clauses to meet specific filtering and sorting requirements.
Updating Data Records (Update)
Updating data in a MySQL database is a crucial aspect of any application. This process allows you to modify existing records, ensuring your data remains accurate and up-to-date. Efficient update mechanisms are essential for maintaining data integrity and responsiveness.
Updating records in a database involves modifying existing data within a specific table. The process requires careful consideration of data integrity and validation to prevent errors and ensure accuracy. Successful updates are critical for maintaining the consistency and reliability of your application’s data.
Methods for Updating Data
The primary method for updating data in a MySQL table is using the `UPDATE` SQL statement. This statement allows you to modify specific columns within rows that match certain criteria. Appropriate use of the `WHERE` clause is essential for targeting the correct records for modification.
Using the UPDATE Statement
The basic structure of an `UPDATE` statement includes the table name, the columns to update, and the conditions to identify the rows to modify.
“`sql
UPDATE table_name
SET column1 = new_value1, column2 = new_value2, …
WHERE condition;
“`
This statement updates the specified columns in the table with the provided new values where the condition is met. The `WHERE` clause is crucial for preventing unintended updates to multiple records.
Example of an UPDATE Statement
Let’s consider a `users` table with columns like `id`, `name`, and `email`. To update the email address of a user with ID 10 to “newuser@example.com”, the following query can be used:
“`sql
UPDATE users
SET email = ‘newuser@example.com’
WHERE id = 10;
“`
This query modifies the `email` column to ‘newuser@example.com’ for the user with ID 10.
Handling Potential Errors
During updates, various errors can occur. These include issues with the data format, constraints, or invalid conditions. Appropriate error handling is essential to maintain application stability.
Using WHERE Clauses for Targeted Updates
The `WHERE` clause is crucial for specifying which rows should be updated. Without a `WHERE` clause, all rows in the table would be updated, which is usually not the desired outcome. The `WHERE` clause allows for selective updates based on specific conditions. For example, to update only users with a specific role, you would include a condition in the `WHERE` clause.
Validating Updated Data
Validating updated data is essential to maintain data integrity. This ensures that the new values meet the defined constraints, such as data types, lengths, and range limitations. A robust validation process prevents invalid or unexpected data from being stored in the database.
Example of PHP Code for Updating Records
“`php
connect_error)
die(“Connection failed: ” . $conn->connect_error);
// Update query
$sql = “UPDATE users SET email = ‘newuser@example.com’ WHERE id = 10”;
if ($conn->query($sql) === TRUE)
echo “Record updated successfully”;
else
echo “Error updating record: ” . $conn->error;
$conn->close();
?>
“`
This PHP code demonstrates a basic update process, including error handling for database connection and query execution. This is a fundamental example, and more complex applications would incorporate more robust error handling and input validation.
Deleting Data Records (Delete)
Deleting data is a crucial aspect of any database application. Properly handling deletions ensures data integrity and prevents accidental loss of important information. This section details how to delete data from a MySQL table using PHP, including best practices for handling sensitive data and implementing soft deletes.
Deleting Records with PHP
Deleting records from a MySQL table involves constructing a SQL query to specify the records to be removed and executing it using a PHP script. This process typically involves using a prepared statement to prevent SQL injection vulnerabilities.
Code Examples for Deleting Records
The following example demonstrates deleting a record from a `users` table based on a specific `user_id`:
“`php
connect_error)
die(“Connection failed: ” . $conn->connect_error);
// Example using a prepared statement
$stmt = $conn->prepare(“DELETE FROM users WHERE user_id = ?”);
$stmt->bind_param(“i”, $user_id);
$user_id = 123; // Replace with the actual user ID
$stmt->execute();
if ($stmt->affected_rows > 0)
echo “Record deleted successfully”;
else
echo “No record found with the given ID.”;
$stmt->close();
$conn->close();
?>
“`
This code snippet uses a prepared statement, protecting against SQL injection. Replace `”your_username”`, `”your_password”`, `”your_database”` with your actual credentials. The `$user_id` variable needs to be properly sanitized to prevent malicious input.
Confirmation Dialogs for Sensitive Data
When deleting sensitive data, a confirmation dialog is essential to prevent accidental deletions. A dialog prompts the user to confirm the deletion, reducing the risk of irreversible actions.
“`html
Delete Record
“`
This example uses JavaScript to create a confirmation dialog before redirecting to the PHP script for deletion. The `id` parameter is crucial for targeting the correct record in the database.
Best Practices for Handling Deletion Errors
Proper error handling is critical in a deletion process. This includes checking if the record exists before attempting deletion and handling potential database errors.
“`php
// … (database connection code) …
if ($stmt->execute())
if ($stmt->affected_rows > 0)
echo “Record deleted successfully”;
else
echo “No record found with the given ID.”;
else
echo “Error deleting record: ” . $stmt->error;
// … (closing statements) …
“`
The code includes error handling. If the deletion fails, an informative error message is displayed.
Implementing Soft Deletes
Soft deletes are a more robust approach for managing deletions than hard deletes. Soft deletes mark a record as deleted but do not physically remove it from the database. This allows for the potential recovery of the data later if needed. This approach is beneficial for auditing purposes or when there’s a need to keep historical records.
A new column, `deleted_at`, is often added to the table.
Implementing Security Measures
Protecting your CRUD application from malicious attacks is crucial. Robust security measures safeguard user data and maintain the integrity of your system. This section details essential techniques to prevent SQL injection, secure password handling, and maintain secure session management.
Implementing proper security practices is not just a matter of compliance; it’s essential for maintaining user trust and preventing data breaches, which can have serious consequences.
Preventing SQL Injection
SQL injection vulnerabilities arise when untrusted data is inserted into SQL queries without proper sanitization. Attackers can exploit these vulnerabilities to execute malicious SQL commands, potentially gaining unauthorized access to your database. To mitigate this risk, always use parameterized queries or prepared statements.
Input Validation and Sanitization
Input validation and sanitization are fundamental security practices. These techniques ensure that user input conforms to expected formats and removes potentially harmful characters. Validate data types, lengths, and ranges. Sanitize input to remove special characters or scripts that could be used to manipulate queries. Regular expressions can help with complex validation tasks.
Using Prepared Statements
Prepared statements are a powerful technique to prevent SQL injection. They separate the SQL query from the input data. This crucial separation prevents attackers from injecting malicious code into the query. Database libraries in PHP provide easy access to prepared statements, significantly enhancing security. For instance, using PDO (PHP Data Objects) with prepared statements ensures that user input is treated as data, not as part of the query itself.
Example using PDO
“`php
prepare(“SELECT
– FROM users WHERE username = :username”);
$stmt->execute([‘username’ => $_POST[‘username’]]);
?>
“`
This example demonstrates how a prepared statement prevents SQL injection. The user input `$_POST[‘username’]` is treated as a parameter, not part of the query string.
Secure Password Handling
Storing passwords in plain text is extremely risky. Implement a strong hashing algorithm to store password hashes, not the raw passwords. Always use a one-way hashing function, like bcrypt or Argon2. Never attempt to decrypt or reverse-engineer hashed passwords.
Importance of Session Management
Secure session management is critical for protecting user data and preventing unauthorized access. Use strong session identifiers, and ensure they are not easily guessable. Employ secure methods for storing session data, such as using a database or a dedicated session storage mechanism.
Secure Session Management Techniques
- Use HTTPS for all communication to encrypt session data during transmission.
- Employ strong session IDs to prevent session hijacking.
- Implement session timeout mechanisms to automatically log out inactive users.
- Regularly rotate session keys to enhance security and mitigate potential vulnerabilities.
Data Validation and Error Handling
Robust data validation and effective error handling are crucial for building reliable and user-friendly applications. Proper validation prevents unexpected behavior and ensures data integrity, while good error handling provides informative feedback to users and helps in debugging. This section Artikels essential validation rules, error handling strategies, and user-friendly error messaging.
Validation Rules for Different Data Types
Validating input data is vital to prevent unexpected issues and maintain data integrity. These rules ensure that data conforms to the expected structure and format.
- Integers: Check if the input is a valid integer. Ensure the input is within the acceptable range to prevent overflow or underflow errors. This often involves using functions like `is_int()` or `ctype_digit()` in PHP, along with range checks.
- Strings: Validate string length, acceptable characters (e.g., alphanumeric, email format), and other specific requirements. Regular expressions are powerful tools for string validation.
- Dates: Ensure the input conforms to a valid date format. Use date parsing functions to convert the input into a usable date object and verify that it falls within the expected range.
- Email Addresses: Validate email addresses using a regular expression to ensure that the format is correct. This helps prevent invalid email addresses from being stored in the database.
- File Uploads: Validate file types, sizes, and extensions. This is critical to maintain security and prevent malicious file uploads.
Methods for Handling Various Error Types
Effective error handling is essential for preventing application crashes and providing useful feedback to users.
- Database Connection Errors: Implement error handling for database connection failures. Use `try…catch` blocks or similar mechanisms to gracefully handle exceptions that may arise during database interactions. Log errors for debugging.
- Validation Errors: Handle validation errors separately from other errors. Display clear and concise error messages to the user, guiding them on how to correct the input. A dedicated section or form element for error messages will help in user experience.
- Input Validation Errors: Use input validation functions to check for unexpected characters, malformed data, or missing required data.
Designing User-Friendly Error Messages, CRUD app tutorial PHP MySQL
User-friendly error messages improve the user experience.
- Clear and Concise Messages: Avoid technical jargon and use simple language to explain the error to the user. Provide specific information on what went wrong and how to correct it.
- Specific Error Messages: Provide different error messages for different types of validation failures. For instance, display a different message for an invalid email format compared to a missing required field.
- Placement of Error Messages: Place error messages close to the corresponding input fields for better context. This improves user understanding and allows for immediate correction.
Handling Validation Errors in PHP
Example of handling a validation error for an integer input.
“`PHP
“`
Table of Error Types and Solutions
This table summarizes different error types and corresponding solutions.
| Error Type | Description | Solution |
|---|---|---|
| Invalid Input | User enters incorrect data format | Use input validation functions and display specific error messages. |
| Database Connection Error | Failed to connect to the database | Use `try…catch` blocks and log the error for debugging. |
| Validation Error | Input data does not meet the validation criteria | Display user-friendly error messages near the input fields. |
| Security Vulnerability | Input data could be exploited | Implement security measures like input sanitization. |
User Interface Design

Source: tutussfunny.com
A well-designed user interface (UI) is crucial for a successful CRUD application. A user-friendly interface ensures intuitive navigation and data manipulation for users. This section details the essential components of a user-friendly UI for a CRUD application, focusing on HTML forms, CSS styling, and responsive design.
Effective UI design is paramount for user satisfaction and application adoption. Clear and consistent design elements contribute to a positive user experience. The use of intuitive controls and a well-organized layout further enhance the overall usability.
HTML Forms for User Interaction
HTML forms are fundamental for user interaction in a CRUD application. They enable users to input, update, and delete data. The structure of these forms dictates how users interact with the application, and careful design is vital.
- Input fields are essential for capturing data. These can include text boxes, drop-down menus, checkboxes, and radio buttons, tailored to the specific data types.
- Buttons, such as “Submit,” “Save,” “Update,” and “Delete,” are critical for triggering actions.
- Labels provide context for input fields, improving clarity and usability.
- Validation is incorporated to ensure data integrity and prevent errors. This includes checking for required fields, valid formats, and ranges.
A well-structured table showcasing the form structure enhances understanding.
| Form Element | Description | Example |
|---|---|---|
| Input Text | Allows users to enter text | |
| Input Email | Allows users to enter an email address | |
| Select | Allows users to choose from a predefined list | |
| Textarea | Allows users to enter multiline text | |
| Button | Triggers an action |
CSS Styling for UI Enhancement
CSS is used to style the UI elements, enhancing visual appeal and consistency. A well-defined CSS style sheet ensures that the application looks visually appealing and aligns with brand guidelines.
- CSS styles are used to control colors, fonts, sizes, and spacing of elements. Using a consistent color scheme and font enhances visual appeal.
- Styling of forms ensures clear visual separation between different input fields and buttons.
- CSS classes and IDs are utilized for targeted styling and maintainability. Using these allows for efficient changes to the visual design.
User-Friendly Layout for CRUD Operations
A well-organized layout improves the user experience. A structured layout makes it easy to locate and interact with different elements.
- The layout should be organized logically, grouping related elements together. This could include sections for data entry, display, and actions.
- Clear visual cues should guide users through the different stages of the CRUD operations.
- Proper spacing and alignment between elements enhance readability and reduce visual clutter.
Responsive Design for Different Screen Sizes
Responsive design is essential for adapting the UI to various screen sizes. It ensures that the application functions smoothly across different devices, like desktops, tablets, and mobile phones.
- Responsive design employs techniques to adjust the layout and elements to different screen widths. Media queries are commonly used to adjust styles based on screen size.
- Elements should resize and rearrange themselves dynamically based on the screen size, preventing layout issues.
- Images should be optimized for different resolutions to maintain visual quality across different devices.
Testing and Debugging: CRUD App Tutorial PHP MySQL

Source: elightwalk.com
Thorough testing and debugging are crucial for ensuring the reliability and functionality of a CRUD application. Robust testing strategies, coupled with effective debugging techniques, minimize errors and enhance the user experience. Comprehensive testing helps identify potential issues before deployment, while debugging allows for swift resolution of any problems that arise.
A well-tested CRUD application guarantees data integrity, accuracy, and efficient operation. Debugging empowers developers to pinpoint and fix errors systematically, ensuring the application functions as intended. This approach reduces downtime and maintains user trust.
Testing Strategies
A well-defined testing strategy is essential for identifying defects and validating the functionality of a CRUD application. This involves establishing test cases that cover various scenarios, from simple data interactions to more complex operations. A robust testing strategy minimizes risks and helps ensure the application meets the specified requirements.
- Unit testing focuses on individual components of the application, such as database interactions or data validation functions. This ensures that each part operates correctly in isolation.
- Integration testing verifies the interaction between different modules or components. This approach ensures that the components work seamlessly together.
- System testing evaluates the entire CRUD application in a simulated or real-world environment. This comprehensive approach identifies potential issues that might not be apparent during unit or integration testing.
- User acceptance testing involves testing the application from the end-user’s perspective. Real users evaluate the application’s usability, functionality, and overall user experience.
Test Cases for CRUD Operations
Test cases are essential for verifying the correctness of each CRUD operation. Each case should cover different input scenarios, including valid and invalid data, boundary conditions, and edge cases.
- Create: Test cases for creating new records should include scenarios for valid data, incomplete data, and data exceeding constraints. For example, test cases for creating a new user should verify the functionality of data validation rules and constraints. This ensures that the application handles various data inputs correctly.
- Read: Test cases for retrieving data should cover scenarios for searching for specific data, retrieving all records, and retrieving data based on specific criteria. For instance, testing a search functionality ensures that the application correctly retrieves the records matching the criteria.
- Update: Test cases for updating records should cover valid data updates, invalid data updates, and updates that involve constraints or triggers. For instance, updating a user’s password should verify the password strength rules.
- Delete: Test cases for deleting records should cover scenarios for deleting specific records, deleting all records, and handling constraints or dependencies. Deleting a user account should ensure associated data is also deleted as necessary.
Debugging Techniques
Debugging involves identifying and fixing errors in the application. A systematic approach, combining various debugging techniques, helps pinpoint the source of errors effectively.
- Print Statements: Strategic print statements in the code help visualize variable values and trace the execution flow. This method is useful for understanding the application’s behavior at different stages.
- Breakpoints: Setting breakpoints in the code allows developers to pause execution and examine variables at specific points. This method helps understand the flow of the application.
- Logging: Comprehensive logging mechanisms provide valuable information about application events, including errors, warnings, and debug messages. This is vital for understanding the context of errors.
Error Logging and Debugging Best Practices
Proper error logging is crucial for tracking issues and facilitating debugging. This approach allows for the analysis of errors and efficient problem-solving.
- Structured Logging: Using a structured logging format (e.g., JSON) provides clear and organized information about errors, including the time, location, and details of the error. This facilitates analysis and debugging.
- Error Handling: Implementing robust error handling mechanisms in the code catches and reports errors effectively. This prevents unexpected crashes and provides structured information.
- Descriptive Error Messages: Providing informative and detailed error messages helps developers understand the cause of the error and take corrective action. Clear error messages are essential for debugging.
Testing Methods
The following table Artikels various testing methods for the CRUD application.
| Testing Method | Description | Purpose |
|---|---|---|
| Unit Testing | Testing individual components in isolation. | Verify individual units of code function correctly. |
| Integration Testing | Testing the interaction between different components. | Ensure components work together seamlessly. |
| System Testing | Testing the entire system in a simulated environment. | Validate the complete functionality of the application. |
| User Acceptance Testing | Testing the application from the end-user perspective. | Ensure the application meets user requirements and expectations. |
Final Conclusion
This CRUD app tutorial PHP MySQL guide provides a structured approach to building robust web applications. You’ll gain hands-on experience in creating, reading, updating, and deleting data within a MySQL database using PHP. This tutorial will empower you to design and implement effective CRUD applications, incorporating best practices and security measures. From basic concepts to advanced techniques, you’ll be equipped to build dynamic and reliable web applications.












Post Comment