The Best Security Software For Protecting Your Computer In 2025
The Best Security Software for Protecting Your Computer in 2025—cyber threats are evolving faster than ever. Staying safe online demands more than just a basic antivirus. This guide dives deep into the top security software options, exploring everything from the latest threats to the most effective protection strategies. We’ll compare top providers, dissect key features, and equip you with the knowledge to safeguard your digital life in the ever-changing landscape of 2025.
From robust antivirus solutions to advanced anti-malware tools and firewalls, we’ll uncover the best options for your needs. Whether you’re a home user, a small business owner, or a large enterprise, we’ll tailor our recommendations to your specific requirements. We’ll also examine crucial aspects like installation, configuration, and ongoing maintenance, making sure your security strategy is not just effective, but also easy to implement.
Plus, we’ll explore future trends and anticipate the challenges and opportunities that lie ahead.
Introduction to Computer Security Software
In 2025, the digital world is more intertwined with our lives than ever before. From banking transactions to healthcare records, our sensitive data resides online, making robust computer security software paramount. This necessitates a deep understanding of the ever-evolving threats and the various tools available to combat them. Failing to prioritize cybersecurity can lead to significant financial losses, reputational damage, and even legal repercussions.The threat landscape is constantly shifting, with new malware strains and sophisticated cyberattacks emerging at an alarming pace.
Phishing scams, ransomware attacks, and data breaches are no longer confined to large corporations; they are increasingly targeting individuals and small businesses, exploiting vulnerabilities in personal devices. This evolving threat necessitates continuous adaptation and vigilance in protecting our digital assets.
Different Types of Security Software
Security software is a multifaceted approach, encompassing a range of tools to safeguard your computer from a diverse array of threats. This includes antivirus, anti-malware, firewalls, and more. Understanding the distinct functions of each type is crucial for choosing the right protection.
Antivirus Software
Antivirus software is designed to detect and remove known viruses from your system. These programs typically scan files, applications, and downloads for malicious code. They rely on signature-based detection, identifying known threats from a database. However, they can struggle with new and unknown threats. Furthermore, proactive scanning and real-time protection are important features.
Antivirus software often incorporates heuristics, which analyze files based on suspicious behavior patterns, to increase detection of unknown threats. Real-world examples include the detection of malware like WannaCry or NotPetya, which caused widespread damage through exploiting known vulnerabilities.
Anti-Malware Software
Anti-malware software expands upon antivirus by targeting a wider range of malicious software, including Trojans, spyware, ransomware, and rootkits. It goes beyond just viruses to encompass a broader spectrum of threats. Anti-malware software often utilizes advanced techniques like behavioral analysis, examining how a program behaves to identify potential threats. Examples include the detection and removal of malicious scripts, malicious extensions, and browser hijackers.
Firewall Software
A firewall acts as a barrier between your computer and the internet, controlling network traffic to prevent unauthorized access. It monitors incoming and outgoing connections, blocking suspicious activity. Firewalls are crucial for preventing hackers from gaining access to your computer or network. They can prevent unauthorized access to your system by blocking malicious traffic. A firewall is a crucial component of a comprehensive security strategy, as it can prevent malicious activity by blocking unauthorized network traffic.
Comparison of Security Software Functionalities
| Feature | Antivirus | Anti-malware | Firewall ||—|—|—|—|| Protection against Viruses | High | Medium | Low || Protection against Malware | Medium | High | Low || Network Protection | Low | Low | High |
Top Security Software Providers in 2025
The digital landscape of 2025 will be significantly more complex, demanding sophisticated security measures to protect individuals and organizations. Cyber threats are constantly evolving, with new vulnerabilities and attack vectors emerging at an alarming rate. This necessitates a robust security infrastructure, relying on the expertise and innovation of top-tier providers to safeguard against these ever-present threats.The leading security software providers in 2025 will be those that have proven their ability to adapt to the evolving threat landscape, integrating cutting-edge technologies and continuously improving their product offerings.
These providers will not only focus on traditional security measures but also embrace proactive defense strategies, predictive analytics, and AI-powered threat detection to stay ahead of malicious actors.
Leading Security Software Providers
The security software market in 2025 will be dominated by a few key players. These companies will have a strong history of innovation, a proven track record, and a large user base, underpinning their position as industry leaders. Their influence will extend beyond providing basic security tools, extending into areas like cloud security, endpoint protection, and advanced threat intelligence.
Market Share and User Base Comparison
While precise market share figures for 2025 are impossible to predict, several companies are poised to hold significant market share. Historically, companies like NortonLifeLock, McAfee, and Trend Micro have established strong positions. However, newer entrants with innovative approaches and strong backing may challenge these established players. The user base will likely reflect these market share dynamics, with companies that adapt and innovate having larger user communities.
Key Strengths and Weaknesses of Leading Providers
The following table Artikels potential strengths and weaknesses of prominent security software providers, recognizing that these are projections based on current trends and market analysis.
| Provider | Strengths | Weaknesses |
|---|---|---|
| NortonLifeLock | Strong brand recognition, extensive product portfolio (covering various aspects of digital security), established user base, and considerable market presence. | Potential challenges in keeping pace with rapid technological advancements, and adapting to new security threats and evolving market demands. Some users may find their pricing strategy to be overly expensive for basic security packages. |
| McAfee | Well-established history in the security industry, offering comprehensive security solutions. | Potential challenges in innovating at a pace matching competitors, and a history of adapting to changing security trends may not be as responsive as newer entrants. Maintaining a strong user base in the face of intense competition will be critical. |
| Trend Micro | Focus on advanced threat detection, utilizing machine learning and AI-powered security solutions. Strong reputation for proactive security measures. | Potential challenge in balancing advanced features with affordability for the mass market, potentially hindering accessibility and broader market penetration. |
| Sophos | Strong reputation for reliability and ease of use, focusing on security solutions tailored for businesses and organizations. | Potential challenge in expanding their reach to the consumer market. |
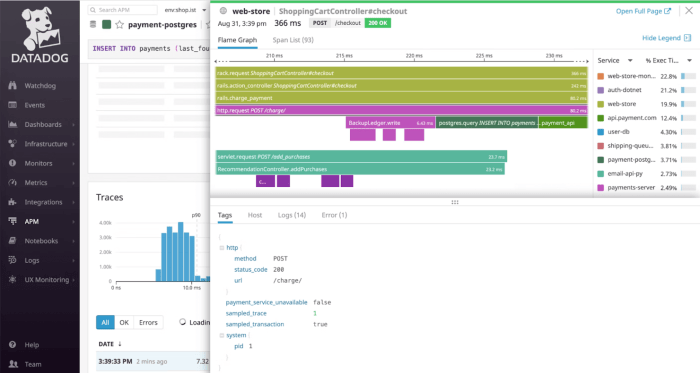
Key Features and Benefits of Top Security Software
Source: thectoclub.com
Staying safe online in 2025 requires more than just a basic antivirus. Top-tier security software now offers a suite of features designed to proactively protect your digital life from sophisticated threats. These tools are no longer just reactive; they’re proactive, offering advanced defenses against emerging cyber dangers.
Real-time Threat Detection
Real-time threat detection is a crucial component of modern security software. These systems constantly monitor your computer’s activity for suspicious patterns and behaviors, instantly identifying and quarantining potential threats before they can cause damage. This proactive approach is far more effective than simply reacting to infections. Think of it like having a vigilant security guard constantly patrolling your digital property.
Sophisticated algorithms analyze network traffic, file activity, and application behavior, flagging anomalies that could signal malware or other malicious intent. This constant vigilance significantly reduces the risk of compromise.
Malware Removal
Top security software goes beyond simple detection; it excels at removing malicious software. Advanced tools use sophisticated algorithms and signature databases to identify and neutralize a wide range of malware types, including viruses, ransomware, spyware, and adware. This comprehensive removal process is critical to restoring a compromised system to its pristine state. The software needs to be continuously updated to recognize and neutralize new threats as they emerge.
Regular updates and automatic scans are essential for effective malware removal.
Vulnerability Scanning
Proactive vulnerability scanning is another key feature of robust security software. These programs identify potential weaknesses in your system’s configuration, applications, and operating system. By pinpointing these vulnerabilities, they empower you to address them before malicious actors exploit them. Imagine a security audit for your computer, proactively identifying potential entry points for attackers. This preventative measure is a cornerstone of modern cybersecurity.
This includes scanning for outdated software, weak passwords, and misconfigurations, helping to create a more secure overall system.
Comparison of Security Features
Security Software for Specific User Needs: The Best Security Software For Protecting Your Computer In 2025
Protecting your digital life isn’t a one-size-fits-all endeavor. Different user groups face varying threats and have different levels of technical expertise. Understanding these nuances is crucial for choosing the right security software. A tailored approach ensures that your digital fortress is as strong as it needs to be, regardless of whether you’re a home user, a small business owner, or a large enterprise.
Home User Security Needs, The Best Security Software for Protecting Your Computer in 2025
Home users, often juggling personal devices and online activities, need comprehensive protection against viruses, malware, and online threats. Simple yet robust security software is key. A strong antivirus program with real-time protection is essential. Privacy concerns are also paramount, so software that protects browsing history and personal data is highly beneficial. Additionally, home users might need parental controls to monitor and safeguard their children’s online activities.
Protecting against phishing attempts and fraudulent websites is critical, as these attacks often target individual users.
Small Business Security Needs
Small businesses face a unique set of security challenges. They often operate with limited IT resources and need security software that is easy to implement and manage. Data breaches can be devastating to small businesses, so robust protection against ransomware and data theft is vital. The software needs to be scalable, allowing for future growth and expansion of the business’s online presence.
Protecting sensitive customer data is paramount, necessitating compliance with relevant regulations and industry standards. Email security and protection against malicious attachments are crucial for preventing data leaks and infections.
Enterprise Security Needs
Enterprise-level security demands a far more sophisticated approach. Large organizations handle vast amounts of sensitive data, making them prime targets for sophisticated cyberattacks. Advanced threat detection and response capabilities are crucial. Multi-layered security solutions, incorporating firewalls, intrusion detection systems, and advanced threat intelligence, are typically required. Compliance with industry regulations, like HIPAA or PCI DSS, is also a major concern, and the security software must integrate with existing systems and workflows.
The software must also support a large number of users, potentially across multiple locations.
Security Needs Table
| User Type | Security Needs | Security Software Recommendation |
|---|---|---|
| Home User | Comprehensive antivirus, real-time protection, parental controls, phishing protection | Sophos Home, Norton AntiVirus Plus, Bitdefender Antivirus Plus |
| Small Business | Robust antivirus, ransomware protection, data loss prevention, email security, scalability | Sophos Intercept X, McAfee Endpoint Security, Trend Micro Worry-Free Business Security |
| Enterprise | Advanced threat detection, multi-layered security, compliance with regulations, large-scale user support, integration with existing systems | CrowdStrike Falcon, Palo Alto Networks, Fortinet FortiGuard |
Security Software Installation and Configuration
Setting up your security software isn’t just about clicking buttons; it’s about proactively safeguarding your digital life. A well-configured system acts as a strong first line of defense against evolving threats, preventing nasty surprises and keeping your precious data safe. Proper installation and configuration are key to realizing the full potential of your security software.Understanding the steps involved in installing and configuring your security software empowers you to make informed choices and ensures your protection is robust and tailored to your needs.
A well-maintained system is a secure system.
Installation Steps
Proper installation is the foundation of a secure system. A poorly installed program might not function as intended, potentially leaving gaps in your overall protection. Carefully following the installation steps minimizes these risks.
| Step | Description |
|---|---|
| Step 1: Download the software | Download the software from the official website or a reputable source. Verify the website’s legitimacy to avoid downloading malicious files. |
| Step 2: Install the software | Follow the on-screen instructions carefully. Avoid rushing through the process. Accept only licenses that align with your understanding and needs. Review the installation path to ensure you understand where the program will be stored. |
| Step 3: Configure the software | Customize settings to match your specific needs and preferences. This includes adjusting scan frequencies, identifying exceptions, and configuring firewall rules. Consider your online habits and what you value most in terms of privacy and security. |
Customizing Security Settings
Optimizing your security software involves customizing settings for maximum protection. Different security needs require varying levels of protection.A tailored approach ensures that the security software aligns with your usage patterns. You might need more aggressive scanning for frequent online shopping or less aggressive scanning for casual social media browsing.
Regular Updates and Maintenance
Regular updates are crucial for maintaining a robust security system. Cybersecurity threats evolve rapidly. Outdated software is more vulnerable to attack.Security software providers regularly release updates to patch vulnerabilities and improve protection against the latest threats. These updates are crucial for staying ahead of evolving cyber threats. Maintaining your software is not just a good practice, but a necessity.
Step-by-Step Guide to Installation and Configuration
1. Download
Download the software from the official website using a secure connection. Check the website’s legitimacy and ensure the download link is authentic.
2. Installation
Follow the on-screen instructions carefully. Review the software license agreement thoroughly before accepting. Ensure you understand where the software is being installed.
3. Configuration
Customize the software’s settings based on your needs. Adjust scan frequencies, define exceptions, and configure firewall rules. Consider how your usage patterns influence your security needs.
4. Regular Updates
Install all available updates promptly. This crucial step keeps the software current and secure against evolving threats. Updates provide the latest protection against emerging threats.
Best Practices for Computer Security in 2025

Source: googleusercontent.com
Staying safe online in 2025 requires more than just a good antivirus. It demands a proactive, multi-layered approach to security, recognizing that cyber threats are constantly evolving. This involves understanding the latest tactics and adapting your habits accordingly. This section details critical best practices for safeguarding your digital life.
Strong Passwords and Multi-Factor Authentication
Robust passwords and multi-factor authentication are the bedrock of online security. Weak passwords are easily cracked, making accounts vulnerable to unauthorized access. Implementing multi-factor authentication adds an extra layer of protection, requiring more than just a username and password to log in.
A strong password is complex, using a combination of uppercase and lowercase letters, numbers, and symbols. Avoid using easily guessable information like birthdays or pet names. Consider using a password manager to generate and store strong passwords securely. Multi-factor authentication (MFA) adds an extra layer of security, often using a code sent to your phone or a dedicated authenticator app.
Safe Browsing Habits and Avoiding Phishing Scams
Navigating the internet safely requires vigilance and awareness. Phishing scams, which attempt to trick you into revealing sensitive information, are a persistent threat. Educating yourself about phishing tactics and practicing safe browsing habits are vital.
Be wary of suspicious emails, websites, and messages. Verify the authenticity of requests for personal information. Avoid clicking on links from unknown senders. Use a reputable anti-phishing tool to detect suspicious websites. Crucially, scrutinize the URL for any inconsistencies or red flags.
Regular Backups and Data Recovery
Regular backups are critical for protecting against data loss due to hardware failure, malware, or accidental deletion. Having a backup strategy ensures that valuable information can be recovered in case of a disaster.
Implement a regular backup schedule. Store backups in a separate location, ideally offline, to protect against data loss from a primary device failure. Test your backup recovery process regularly to ensure your data can be retrieved if needed.
Keeping Software Up-to-Date
Keeping software up-to-date is crucial for patching security vulnerabilities. Software developers regularly release updates that address known security flaws, protecting your system from potential threats.
Enable automatic updates whenever possible. Regularly check for software updates for your operating system, applications, and security software. Cybercriminals exploit known vulnerabilities, so staying ahead of the curve is paramount.
Practical Tips for Computer Security
Beyond the core practices, several practical tips can significantly enhance your computer security posture. These tips emphasize proactive security measures.
- Use a reputable antivirus and anti-malware program.
- Install firewalls to protect your network from unauthorized access.
- Be cautious about downloading files from untrusted sources. Verify the source before downloading any software or file.
- Review and adjust your privacy settings on all your devices and online accounts. Control what information is accessible to others.
- Use strong, unique passwords for every account.
- Avoid using public Wi-Fi networks for sensitive activities. If you must use public Wi-Fi, utilize a virtual private network (VPN).
Future Trends in Computer Security Software
The digital landscape is constantly evolving, demanding constant adaptation in cybersecurity. Protecting our precious data from increasingly sophisticated threats requires proactive measures and a deep understanding of emerging trends. 2025 and beyond will see a surge in innovative security solutions, driven by advancements in AI and the expanding role of cloud computing.Security software is no longer just about antivirus; it’s about anticipating and mitigating a broader spectrum of threats, from sophisticated phishing attempts to the rise of AI-powered attacks.
This evolution necessitates a comprehensive approach to protecting our digital assets.
Emerging Threats and Vulnerabilities
The digital world is a battlefield, and new threats are constantly emerging. Cybercriminals are continuously innovating, developing more sophisticated tactics to bypass existing security measures. This necessitates a proactive approach to threat intelligence and vulnerability analysis, enabling security software to adapt and anticipate these evolving attacks. Examples include ransomware-as-a-service, supply chain attacks targeting software updates, and the rise of deepfakes used for social engineering.
Furthermore, the increasing reliance on interconnected devices (IoT) introduces new attack vectors, requiring specialized security measures to protect these vulnerable networks.
The Role of Artificial Intelligence in Security Software
AI is transforming the cybersecurity landscape. AI-powered tools can analyze vast amounts of data to identify patterns and anomalies indicative of malicious activity, enabling faster detection and response times. Machine learning algorithms can learn from past attacks, adapting security measures in real-time to neutralize new threats. For instance, AI-powered threat detection systems can identify suspicious user behavior, proactively blocking potential intrusions.
This intelligent approach can significantly improve the efficacy of security software in the face of increasingly complex threats.
The Impact of Cloud Computing on Security Software
Cloud computing has revolutionized how we store and access data. This shift also brings unique security challenges. Security software must adapt to protect cloud environments, ensuring data integrity and confidentiality while users access and share information across various platforms. This includes securing cloud storage, preventing unauthorized access, and ensuring compliance with data privacy regulations. Furthermore, the need for secure access control and encryption within cloud-based systems is paramount.
Development of More User-Friendly Interfaces
User experience is paramount in cybersecurity. Security software should be intuitive and easy to use, regardless of technical expertise. This includes clear and concise dashboards, simplified configuration options, and user-friendly reporting tools. The complexity of security protocols shouldn’t deter users from utilizing essential security measures. Clear guidance and interactive tutorials can empower users to proactively manage their digital security.
Last Word
Source: thectoclub.com
Navigating the complex world of computer security in 2025 doesn’t have to be daunting. By understanding the evolving threat landscape, comparing top security software providers, and implementing best practices, you can significantly bolster your online protection. This comprehensive guide empowers you to make informed decisions, safeguard your digital assets, and confidently embrace the digital future. So, equip yourself with the knowledge to stay secure and thrive in the ever-evolving online world.






Post Comment