Virtualization Explained How Vms Work
Virtualization explained how VMs work, providing a comprehensive exploration of this powerful technology. From the fundamental concepts of virtualization to its applications in cloud computing, this guide unravels the mysteries behind virtual machines. We’ll delve into the structure of VMs, explore various hypervisors, and examine their lifecycle and management. Understanding the intricacies of VM storage and networking, along with security considerations, will equip you with a solid grasp of this essential technology.
This guide will break down the complex world of virtualization, offering clear explanations and comparisons. We’ll cover everything from the historical context and benefits of virtualization to the different types of hypervisors and the crucial role they play in VM management. The process of creating, managing, and maintaining virtual machines will be thoroughly detailed, along with insights into virtualization technologies like VMware, VirtualBox, and KVM.
A strong emphasis will be placed on understanding how virtualization plays a critical role in cloud computing, providing a detailed analysis of its applications in IaaS, PaaS, and SaaS services.
Introduction to Virtualization
Virtualization is a powerful technology that allows multiple virtual machines (VMs) to run on a single physical computer. Imagine having multiple computers operating within a single machine, each with its own operating system and applications. This concept, while complex in implementation, simplifies resource management and provides significant flexibility in computing environments.Virtualization essentially creates a virtualized environment where software interacts with virtual hardware, rather than directly with physical hardware.
This separation of software from physical resources allows for increased efficiency, flexibility, and cost savings in many applications.
Fundamental Concept of Virtualization
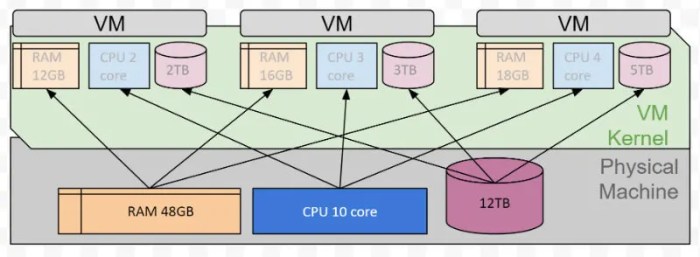
Virtualization abstracts away the physical hardware layer, allowing multiple operating systems and applications to run concurrently on a single physical host. This is achieved by creating virtualized hardware resources such as CPUs, memory, and storage. Each virtual machine (VM) is an isolated environment, independent of other VMs, ensuring that any problems in one VM do not affect the others.
The virtual machine monitor (VMM), also known as a hypervisor, acts as an intermediary between the virtual machines and the physical hardware, managing the allocation and utilization of resources.
History of Virtualization
The concept of virtualization has been evolving for decades. Early forms of virtualization emerged in the 1960s, initially as a way to improve resource utilization in mainframe computers. Key milestones include the development of the first hypervisors in the 1970s and the growing popularity of x86 virtualization in the 2000s, facilitated by advancements in hardware and software. The evolution of virtualization has significantly improved efficiency, allowing for more flexible and cost-effective computing.
For example, cloud computing platforms heavily rely on virtualization technology to deliver scalable and on-demand resources to users.
Benefits of Virtualization
Virtualization offers numerous advantages in diverse contexts. It enables increased resource utilization by running multiple operating systems on a single physical machine, reducing hardware costs. Virtualization also simplifies disaster recovery and business continuity by allowing for easy replication and migration of VMs. Moreover, virtualization enhances application development and testing by providing isolated environments for various applications and operating systems.
Furthermore, virtualization facilitates efficient resource allocation, allowing administrators to scale resources as needed.
Analogy for Virtualization
Imagine a large office building. Instead of each employee having their own private office, a single space is divided into smaller, virtual offices. Each virtual office is equipped with the necessary tools and resources, such as desks, computers, and printers. The building manager (hypervisor) manages the allocation of these resources among the virtual offices. This allows for a more efficient use of space and resources compared to having separate offices for every employee.
Comparison of Physical Servers and Virtual Machines
| Feature | Physical Server | Virtual Server | Key Difference |
|---|---|---|---|
| Hardware | Dedicated physical hardware | Shares physical hardware resources | Virtual servers utilize the resources of a physical server, while physical servers require their own hardware. |
| Operating System | One operating system per server | Multiple operating systems on a single server | Virtualization allows multiple operating systems to run on a single physical server, whereas physical servers can run only one operating system per server. |
| Resource Allocation | Fixed resources per server | Dynamic allocation of resources | Virtualization allows for dynamic allocation of resources to VMs, unlike physical servers, which have static resource allocation. |
| Management | Individual server management | Centralized management of multiple VMs | Virtualization enables centralized management of multiple VMs, simplifying administration and maintenance tasks. |
Virtual Machines (VMs) Explained
Virtual machines (VMs) are software-based representations of physical computers. They allow users to run multiple operating systems and applications on a single physical machine, enhancing resource utilization and flexibility. This approach offers numerous advantages over traditional physical machines, including cost savings and improved operational efficiency.
Structure of a Virtual Machine
A virtual machine’s structure mirrors that of a physical computer. It has its own virtualized hardware components, enabling it to function independently. Crucially, this virtual hardware is managed and controlled by a hypervisor. This separation is fundamental to the operation of a VM.
Components of a Virtual Machine
Virtual machines comprise several key components, each crucial for its functionality. These components include:
- Virtual CPU (vCPU): A virtualized processor that emulates the instructions and operations of a physical CPU. This allows the VM to execute its operating system and applications. The number of vCPUs allocated to a VM impacts its performance and ability to handle tasks.
- Virtual Memory: A portion of the host system’s physical memory allocated to the VM. This virtual memory acts as the RAM for the VM, enabling the execution of programs and processes. The amount of virtual memory affects the VM’s ability to run demanding applications.
- Virtual Storage: A virtual hard drive that emulates the storage space of a physical hard drive. This virtual disk stores the VM’s operating system, applications, and data. The capacity of this virtual storage determines the amount of data the VM can hold.
The Hypervisor: Orchestrating Virtualization
The hypervisor acts as the intermediary between the physical host machine and the virtual machines. It manages the virtual hardware resources and ensures that each VM functions correctly. Essentially, it creates and controls the virtual environment.
Types of Hypervisors
Hypervisors are categorized into two main types:
- Type 1 (Bare-metal) Hypervisors: These hypervisors run directly on the host hardware. They have full control over the system resources, resulting in greater performance and efficiency. Examples include VMware ESXi and Xen.
- Type 2 (Hosted) Hypervisors: These hypervisors run on top of an existing operating system. They utilize the host OS’s resources, which can slightly impact performance. Examples include VMware Workstation Player and VirtualBox.
VM Performance vs. Physical Machines
Virtual machines generally exhibit slightly lower performance compared to physical machines. This difference arises from the overhead associated with virtualization. The hypervisor needs to manage and allocate resources to each VM, introducing a layer of abstraction. However, the performance difference is often minimal, and VMs can still provide satisfactory performance for many tasks. Furthermore, the gains in flexibility and resource utilization often outweigh the minor performance loss.
Comparison of Type 1 and Type 2 Hypervisors
| Hypervisor Type | Pros | Cons | Use Cases |
|---|---|---|---|
| Type 1 | High performance, efficient resource utilization, direct access to hardware, improved security | Requires specialized knowledge to install and manage, potentially higher initial cost, less flexibility for troubleshooting | Data centers, server farms, virtual desktop infrastructure (VDI) |
| Type 2 | Easy to install and manage, runs on existing OS, lower initial cost, broader range of use cases | Performance can be impacted by host OS, limited control over hardware resources, security risks if host OS is compromised | Personal use, development environments, testing, small to medium-sized businesses (SMBs) |
VM Lifecycle and Management
Virtual machines (VMs) require careful management throughout their lifecycle. From creation to deletion, understanding the process and utilizing appropriate tools is crucial for efficient resource utilization and system stability. Effective VM management ensures smooth operations and minimizes downtime.
VM Creation and Initialization
Creating a VM involves defining its configuration, including the operating system, memory, storage, and network settings. This process typically involves selecting a template or image of the desired operating system and specifying the resources allocated to the virtual machine. Once the configuration is finalized, the VM is initialized and prepared for use.
VM Startup and Shutdown
Starting a VM activates the virtual hardware and loads the operating system. This process can vary depending on the virtualization platform and the configuration of the VM. Stopping a VM gracefully saves the current state of the system, allowing for quick restart and preventing data loss. Forcibly shutting down a VM, however, might lead to data corruption.
VM Deletion
Deleting a VM permanently removes the virtual machine from the system. Before deletion, it’s crucial to ensure all important data has been backed up or saved to other storage. This process varies across different virtualization platforms and tools.
VM Management Tools, Virtualization explained how VMs work
Various tools facilitate the management of virtual machines. These tools offer a range of functionalities, including creating, starting, stopping, and deleting VMs. They also allow for monitoring and managing resources, as well as troubleshooting issues.
VM Maintenance Procedure
- Regularly check VM performance metrics, including CPU usage, memory consumption, and disk I/O. Monitoring helps identify potential bottlenecks or issues.
- Back up virtual machine disks regularly to protect against data loss due to unexpected events, like hardware failure or software errors.
- Update the guest operating system and virtualization platform software to patch security vulnerabilities and improve performance.
- Configure and test disaster recovery procedures for virtual machines to ensure data and system availability in case of failures.
- Properly shut down and power off virtual machines to prevent potential issues and save resources.
Step-by-Step VM Installation
- Install the virtualization software (e.g., VMware Workstation, VirtualBox) on your host operating system.
- Choose an operating system image or template for the virtual machine.
- Specify the resources (RAM, storage) required for the virtual machine.
- Configure the network settings for the virtual machine.
- Start the virtual machine and complete the operating system installation.
VM Management Tools Overview
| Tool Name | Description | Features | Pros/Cons |
|---|---|---|---|
| VMware vSphere | A comprehensive virtualization platform | VM creation, management, resource allocation, clustering | Powerful, robust, but expensive; complex to implement and manage |
| VirtualBox | Open-source virtualization software | Simple VM creation, flexible configuration, good for testing | Free, user-friendly, but limited features for complex deployments |
| Hyper-V | Microsoft’s virtualization platform | Integrated with Windows, good for Windows-based workloads | Good for Windows environments, but limited support for other OS |
| Proxmox | Open-source hypervisor | Excellent performance, supports various OS, good for servers | Requires some technical knowledge, less user-friendly than some other options |
Virtualization Technologies
Virtualization technologies have revolutionized computing by enabling multiple virtual machines (VMs) to run on a single physical host. This approach boosts efficiency, reduces hardware costs, and facilitates flexible resource allocation. Different virtualization technologies offer varying levels of performance, features, and ease of use, each suited to different needs.Several prominent virtualization technologies are available, each with its unique strengths.
These technologies differ in their underlying mechanisms, features, and compatibility with various operating systems. Understanding these distinctions is crucial for selecting the appropriate solution for a given task.
Different Virtualization Technologies
Various virtualization technologies exist, each offering distinct functionalities. These technologies underpin the operation of virtual machines, defining how resources are managed and VMs interact with the physical host. Key examples include VMware, VirtualBox, and KVM, each with its own set of characteristics.
Key Features of VMware
VMware is a widely used virtualization platform known for its comprehensive features and robust performance. It excels in enterprise environments due to its advanced features and support for diverse operating systems. VMware offers a broad range of tools for managing and monitoring virtual machines, including tools for creating and deploying VMs, and for managing storage and networking.
Key Features of VirtualBox
VirtualBox, an open-source virtualization solution, stands out for its ease of use and lightweight nature. Its user-friendly interface makes it ideal for personal use, development, and education. Its open-source nature allows for community-driven development and customization, enabling users to adapt the software to specific needs. Furthermore, VirtualBox is compatible with a wide array of operating systems, extending its applicability across different platforms.
Key Features of KVM
KVM (Kernel-based Virtual Machine) is a powerful, open-source virtualization solution integrated directly into the Linux kernel. This integration provides high performance and efficiency, making it suitable for demanding server environments. KVM’s kernel-level integration translates to optimized resource management and lower overhead compared to other hypervisors. Its flexibility and extensibility through modules make it adaptable to specific use cases.
Comparison of Virtualization Software Packages
Different virtualization software packages cater to varying needs and contexts. The choice depends on factors like the required level of performance, support for specific operating systems, and budget considerations. The following table compares VMware, VirtualBox, and KVM.
| Software Name | Key Features | Use Cases | Limitations |
|---|---|---|---|
| VMware | Robust performance, extensive features, enterprise-grade tools, broad operating system support | Enterprise deployments, server virtualization, complex application environments, high-performance needs | Can be expensive, licensing requirements, complex setup process, potentially high resource consumption |
| VirtualBox | Ease of use, lightweight design, open-source, broad operating system compatibility | Personal use, development environments, educational purposes, simple virtualization tasks | Performance might be lower than VMware or KVM in demanding scenarios, limited enterprise-grade features |
| KVM | High performance, kernel-level integration, open-source, excellent resource utilization | Server virtualization, high-performance computing, cloud environments, Linux-based systems | Requires Linux-based host system, complex configuration for advanced users, might require additional expertise for setup |
Real-World Applications of Virtualization Technologies
Virtualization technologies find widespread use across diverse industries. They enable organizations to efficiently manage resources, streamline workflows, and reduce operational costs. Examples include:
- Cloud Computing: Cloud providers heavily rely on virtualization to create and manage virtual servers, offering scalable and flexible computing resources to clients.
- Software Development: Developers utilize virtual machines to test and debug applications in isolated environments, ensuring compatibility across different operating systems and configurations.
- Disaster Recovery: Virtual machines facilitate rapid disaster recovery by providing a replica of critical systems in a virtual environment, enabling quick restoration in case of physical failures.
- Testing and Training: Virtual machines provide controlled and isolated environments for testing new software and conducting training exercises.
Integration into Existing Systems
Integrating virtualization technologies into existing systems requires careful planning and consideration. The process often involves assessing existing hardware, identifying the appropriate virtualization software, and implementing the necessary configurations. Compatibility issues may arise, necessitating adjustments to existing infrastructure and software.
VM Storage and Networking: Virtualization Explained How VMs Work
Virtual machines (VMs) rely on virtualized storage and networking to function effectively. This critical aspect allows VMs to operate independently while sharing resources with the host system. Understanding how virtual disks are managed, virtual networks are configured, and virtual network adapters connect to physical networks is essential for successful VM deployment and administration.Virtual disks, unlike physical disks, are not directly attached to hardware.
Instead, they are stored as files on the host system’s storage. This file-based approach offers flexibility and scalability. Virtual disks can be easily copied, moved, and backed up.
Virtual Disk Handling
Virtual disks are managed as files within the VM environment. These files can be located on different storage devices, including local storage, network shares, or cloud storage. The virtual machine monitor (VMM) abstracts the underlying storage, providing a consistent interface to the virtual disk regardless of its physical location. The VMM manages the disk’s access and ensures that the VM sees it as a dedicated disk.
This decoupling of storage from physical hardware allows for greater flexibility in storage management and facilitates disaster recovery. Furthermore, different formats for virtual disk images (e.g., VMDK, VHD) exist, each with its own characteristics in terms of performance and compatibility.
Virtual Networks and Configuration
Virtual networks emulate physical networks within a virtual environment. They allow VMs to communicate with each other and with the external world, mirroring real-world network topologies. Virtual networks are configured with parameters such as IP addresses, subnet masks, and gateway addresses. Network configurations can be customized to meet specific needs, such as creating isolated networks for different departments or teams.
This isolation enhances security by preventing unauthorized access between VMs.
Virtual Network Adapters and Physical Network Connections
Virtual network adapters (vNICs) act as the bridge between a VM and the physical network. They allow the VM to access the network and communicate with other VMs or external systems. The vNIC is configured to connect to a virtual network. The configuration determines how the VM interacts with the physical network, whether it’s connected to a specific network segment or a virtual switch.
Virtual switches aggregate multiple vNICs into a single virtual network interface for the host operating system.
Network Settings Configuration
Network settings for a VM are configured through the VM software or the hypervisor. This involves setting the IP address, subnet mask, gateway address, and DNS server information. The settings ensure proper communication between the VM and other network devices. Static IP configurations offer predictable network access, while dynamic IP addresses provided by DHCP are convenient for temporary or mobile VMs.
Network Configurations for VMs
The following diagram illustrates different network configurations for VMs. [Diagram Description: The diagram would show three VMs connected to a virtual switch. VM1 is connected to a network with a public IP address and can access the internet. VM2 is connected to a private network with a specific subnet and can communicate with other VMs within the private network.
VM3 is connected to a virtual switch and uses DHCP for its network configuration.]
Virtual Networking Types
Different types of virtual networking offer varying levels of functionality and security.
| Network Type | Description | Pros | Cons |
|---|---|---|---|
| Bridged Networking | Connects a VM to a physical network as if it were a physical machine. | Provides full access to the physical network, simple configuration for most users. | Potential conflicts with other devices on the physical network, requires careful IP address management. |
| NAT Networking | Uses Network Address Translation to provide the VM with an IP address on the physical network. | Easy setup, no need to configure IP addresses for VMs, ideal for guest VMs. | Performance may be affected by NAT, limited access to external resources. |
| Host-only Networking | Creates a private network between the host and VM. | Isolated network environment, no need for external network access. | Limited external network access, needs extra configuration for VMs communicating with each other. |
| Virtual Switch Networking | Connects multiple VMs to a virtual switch, allowing for isolation and management of network traffic. | Supports advanced networking features, more flexibility than other methods. | Can be complex to configure, might require specialized knowledge. |
Virtualization in Cloud Computing
Virtualization is the cornerstone of modern cloud computing services. It allows multiple virtual machines (VMs) to run on a single physical server, significantly increasing resource utilization and reducing hardware costs. This foundational technology enables the scalability, flexibility, and on-demand provisioning that define cloud offerings.Cloud computing leverages virtualization to provide a flexible and scalable infrastructure. This approach effectively abstracts the underlying hardware, enabling users to access computing resources without needing direct physical interaction.
This model is fundamental to the pay-as-you-go pricing model common in cloud environments.
Virtualization Underpins Cloud Services
Virtualization is integral to all three primary cloud service models: Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS). It creates the virtualized environment where resources are provisioned, managed, and accessed. This virtualized layer separates the underlying physical infrastructure from the applications and services running on top.
Benefits of Virtualization in Cloud Environments
Virtualization offers substantial benefits in cloud settings. These include increased resource utilization, reduced hardware costs, improved agility and scalability, and enhanced security. The ability to rapidly provision and de-provision virtual resources allows cloud providers to efficiently respond to fluctuating demand.
Role of Virtualization in Infrastructure as a Service (IaaS)
In IaaS, virtualization is crucial. It allows cloud providers to pool physical server resources into a shared virtual environment. Users can then provision virtual machines with the specific configurations and operating systems they need. This approach enables pay-as-you-go models where users only pay for the resources they consume. The dynamic nature of virtual machines directly supports the elasticity and scalability demanded by IaaS.
Benefits of Virtualization for PaaS and SaaS Services
Virtualization is also beneficial for PaaS and SaaS. For PaaS, it provides the isolated virtual environments needed to support different applications and development teams. This allows for better resource management and application isolation, improving development efficiency and security. In SaaS, virtualization facilitates the deployment and scaling of applications to a large number of users.
Diagram Illustrating Virtualization in Cloud Infrastructure
(Imagine a diagram here showing a physical server with multiple virtual machines running on it. The virtual machines would be represented as separate containers, each with its own operating system and applications. A cloud interface would connect to these VMs.) The diagram would visually represent the abstraction of the physical hardware layer, highlighting how multiple virtualized resources are available to users through the cloud interface.
Comparison of Cloud Virtualization Platforms
| Platform Name | Features | Scalability | Cost |
|---|---|---|---|
| VMware vSphere | Mature, comprehensive platform with strong integration capabilities. | Highly scalable, supporting large-scale deployments. | Generally considered higher upfront cost, but with potential for long-term savings due to efficiency. |
| Microsoft Azure Virtual Machines | Robust platform with a wide range of configurations and integrations. | Highly scalable, able to handle significant workloads and user demands. | Pay-as-you-go pricing model, with costs variable depending on resource utilization. |
| Amazon Web Services (EC2) | Industry-leading platform with a large ecosystem of services and integrations. | Extremely scalable and highly available. | Competitive pay-as-you-go pricing, with diverse options for customization. |
| OpenStack | Open-source platform offering flexibility and customization. | Scalable to a large degree, depending on deployment choices. | Generally lower upfront costs, but with potential for higher operational costs depending on internal expertise. |
Security Considerations in Virtualization
Virtualization, while offering numerous benefits, introduces unique security challenges. The shared nature of resources and the potential for vulnerabilities in the hypervisor itself require careful consideration and robust security measures. Understanding these implications is crucial for maintaining the integrity and confidentiality of data hosted within virtualized environments.
Security Implications of Virtualization Environments
Virtualization environments, with their shared infrastructure, can create unforeseen security vulnerabilities. A compromised virtual machine (VM) can potentially impact other VMs on the same host, creating a cascading effect. Moreover, the complex interplay between VMs, hypervisors, and underlying physical infrastructure requires a multifaceted security approach. Misconfigurations or inadequate security controls can lead to data breaches, unauthorized access, and denial-of-service attacks.
Potential Vulnerabilities and Risks Associated with VMs
Several vulnerabilities can arise within virtualized environments. Malicious code injected into a VM can exploit vulnerabilities in the hypervisor or other VMs. This necessitates stringent security controls for guest VMs, as well as for the hypervisor itself. Furthermore, the ease of creating and deploying VMs can make them attractive targets for attackers seeking to establish a foothold within a network.
Strategies for Securing VMs and Hypervisors
Robust security strategies are essential for protecting virtualized environments. Regular security audits and penetration testing can help identify vulnerabilities. Implementing strong access controls and enforcing strict authentication mechanisms is crucial for restricting unauthorized access. Using encryption to protect sensitive data, both in transit and at rest, is a fundamental security practice. Regular patching and updates for both the hypervisor and guest VMs are vital for mitigating known vulnerabilities.
Security Best Practices for Virtualization Deployments
Adhering to best practices is paramount for securing virtualization deployments. Implementing a layered security approach, incorporating firewalls, intrusion detection systems, and other security tools, is essential. Regular backups and disaster recovery plans are vital for mitigating the impact of security incidents. A security awareness program for personnel working with virtualization environments is essential for maintaining a strong security posture.
Employing a zero-trust security model, where every entity is treated as potentially untrusted, can further enhance security.
Table: Security Risks in Virtualization Environments
| Risk Type | Description | Mitigation Strategies | Prevention Measures |
|---|---|---|---|
| Hypervisor vulnerabilities | Exploitable weaknesses in the hypervisor software itself can allow malicious actors to gain control of the entire virtualization environment. | Regularly update and patch the hypervisor. Employ intrusion detection systems. | Conduct regular security audits of the hypervisor. Implement strong access controls. |
| Guest VM compromise | A compromised guest VM can be used to attack other VMs, the hypervisor, or the underlying physical host. | Implement strong access controls for each VM. Employ anti-malware solutions within VMs. | Regularly scan and update guest VMs. Employ host-based firewalls. |
| Network security issues | Virtualized environments share networks, potentially creating vulnerabilities if network security measures are not implemented correctly. | Segment networks and use VLANs to isolate VMs. Implement network access controls. | Regularly audit network configurations. Enforce strong network security policies. |
| Data breaches | Sensitive data residing within VMs can be vulnerable if appropriate security measures aren’t in place. | Employ encryption for data at rest and in transit. Implement data loss prevention (DLP) tools. | Regularly back up data and implement robust recovery plans. |
Conclusive Thoughts
Source: cloudinary.com
In summary, Virtualization explained how VMs work by presenting a detailed overview of this transformative technology. We’ve explored the core concepts, from the structure of virtual machines to the various virtualization technologies. This guide has highlighted the critical role of virtualization in cloud computing and the key security considerations for successful implementation. By understanding these fundamentals, you can leverage virtualization to enhance efficiency, scalability, and security in your computing environment.












Post Comment