History Of Cybersecurity And Computer Viruses
History of cybersecurity and computer viruses traces the evolution of digital threats from early computing systems to the sophisticated attacks of today. This journey reveals the fascinating interplay between malicious code and the development of defenses, showcasing how our understanding of security has adapted to new technologies and threats.
From simple pranks to advanced persistent threats, the story of computer viruses and the fight against them is a dynamic and ever-evolving narrative. The emergence of the internet dramatically altered the landscape, introducing new vulnerabilities and necessitating the development of sophisticated security protocols. This evolution, driven by both malicious actors and defenders, highlights the constant tension between innovation and security.
Early Days of Computing and Security Threats
The dawn of computing brought forth not only incredible advancements but also early vulnerabilities. As the technology evolved, so did the understanding of potential threats, paving the way for the field of cybersecurity. Early systems, while rudimentary by today’s standards, were surprisingly susceptible to manipulation, laying the groundwork for the security challenges we face today.The earliest computing environments, often centralized and reliant on limited resources, had inherent security weaknesses.
These vulnerabilities were exploited in various ways, from simple data breaches to more sophisticated attacks. The development of countermeasures, and the realization of the need for robust security, was a direct response to these early incidents.
Early Computing Systems and Vulnerabilities
Early computing systems, primarily mainframe computers, were large, complex, and often housed in secure, dedicated facilities. Access was tightly controlled, but the sheer complexity of these systems made them vulnerable to a variety of issues. Hardware failures, software bugs, and even simple human errors could disrupt operations. The lack of sophisticated security protocols made these systems susceptible to unauthorized access and modification of data.
First Documented Instances of Malicious Code
The very first instances of malicious code were rudimentary compared to modern viruses. Early “viruses” were often accidental errors in programs, or, in some cases, deliberate attempts to disrupt operations. These were not self-replicating like modern viruses, but they still demonstrated the potential for malicious intent in software. One notable example of early malicious code was the creation of “logic bombs” that were triggered by specific events, like a date or a particular file being accessed.
These actions highlighted the potential of exploiting software vulnerabilities.
Key Technologies and Concepts in Early Cybersecurity
In the early days of computing, the security measures were often rudimentary, often involving physical access controls and simple password systems. The concept of user authentication and authorization, though in its infancy, was emerging as a fundamental element in protecting data. Access controls, physical and logical, were the cornerstones of securing early computer systems. The idea of creating secure software and systems was beginning to emerge, although the terminology and understanding were not as developed as they are today.
Timeline of Significant Events Influencing Cybersecurity
- 1940s-1950s: The development of early computers and the first concepts of programming and software. This era saw the emergence of the first potential security issues, though the term “cybersecurity” did not exist. The focus was more on reliability and functionality rather than explicit security measures.
- 1960s: The creation of the ARPANET, the precursor to the internet. This development brought new challenges in terms of security, as communication between different systems became more complex. The concept of network security began to take shape.
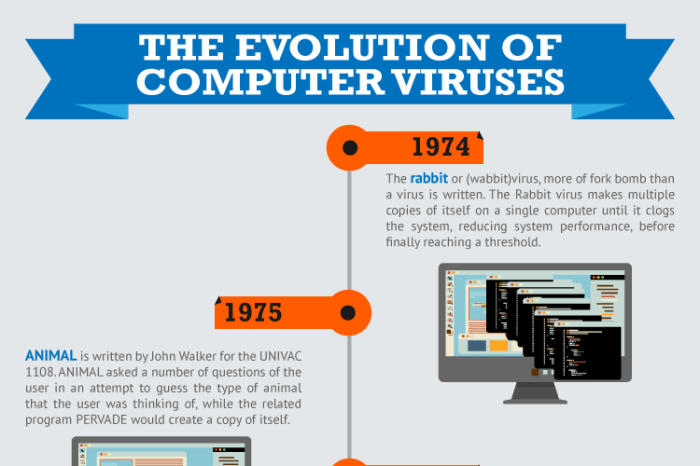
- 1970s: The emergence of the first computer viruses. The creation of the first computer worms marked a critical turning point in the evolution of malicious software. These events highlighted the potential for malicious code to spread and cause harm.
- 1980s: The proliferation of personal computers and the increasing reliance on networked systems. This period saw a dramatic rise in the number of potential vulnerabilities and the need for robust security measures. The need for user education on security awareness also started to become important.
- 1990s: The growth of the internet and the development of sophisticated malware. The rise of the internet led to a significant increase in the complexity and scale of attacks, demanding more sophisticated security tools and techniques.
Comparison of Early and Modern Computing Environments
| Feature | Early Computing Environments | Modern Computing Environments |
|---|---|---|
| Hardware | Large mainframe computers, centralized locations | Diverse hardware, including personal computers, mobile devices, cloud servers |
| Software | Limited software options, primarily batch processing | Vast software ecosystems, including operating systems, applications, and cloud services |
| Security Measures | Physical access controls, rudimentary passwords, limited user accounts | Multi-layered security protocols, including firewalls, intrusion detection systems, and advanced authentication methods |
| Network Connectivity | Limited or nonexistent network connectivity | Ubiquitous network connectivity, with a complex network of interconnected systems |
| Data Storage | Magnetic tapes, hard drives of limited capacity | Vast data storage capacity, including cloud storage and distributed systems |
The Rise of Computer Viruses and Worms

Source: mahmudan.com
The early days of computing, while pioneering, were vulnerable to malicious intent. As computer systems became more interconnected and accessible, so did the potential for harmful code to spread. The evolution of computer viruses and worms reflects a progression from playful pranks to sophisticated attacks, demonstrating the escalating sophistication of malicious actors.The development of computer viruses and worms wasn’t an immediate leap from benign code to destructive tools.
It was a gradual process, beginning with relatively simple programs and escalating in complexity over time. The early motivations were often rooted in experimentation, intellectual curiosity, or even a desire to demonstrate technical prowess. However, as the technology matured, so did the malicious intent and the potential for widespread damage.
Evolution of Malware from Simple Pranks to Sophisticated Attacks
Early computer viruses and worms were often little more than harmless pranks, designed to spread amusing messages or cause minor disruptions. However, as the technology advanced, so did the sophistication of these attacks, transitioning from simple annoyances to significant security threats. This evolution was driven by the increasing interconnectedness of computer systems and the growing understanding of how code could be manipulated to achieve malicious goals.
Different Types of Malware and Their Characteristics
Early malware manifested in diverse forms. Boot sector viruses, for example, targeted the master boot record of a hard drive, disrupting the operating system’s startup process. File infectors, on the other hand, attached themselves to executable files, replicating and spreading with each file’s execution. These early viruses typically relied on relatively simple methods of propagation, such as floppy disks and email attachments.
Later, the rise of the internet provided new avenues for propagation, paving the way for more complex and widespread attacks.
Notable Early Viruses and Their Impact
One of the most well-known early viruses is the “Elk Cloner,” which infected Apple II systems in the 1980s. While not devastating, it demonstrated the potential for viral replication and the difficulty in containing such infections. The “Morris Worm,” released in 1988, had a far more significant impact. It exploited vulnerabilities in Unix systems, causing widespread disruptions across the nascent internet, and highlighting the vulnerability of interconnected networks to malicious code.
Comparison of Early and Modern Virus Propagation Methods, History of cybersecurity and computer viruses
Early viruses often relied on physical media like floppy disks and network shares. Modern methods leverage the internet, email, and social media platforms, dramatically expanding the potential reach and speed of propagation. Sophisticated techniques, such as phishing scams and exploiting software vulnerabilities, have also emerged, making detection and containment more challenging.
Motivations Behind Early Virus Creation
The motivations behind early virus creation were multifaceted. Some individuals created viruses out of a sense of intellectual curiosity or a desire to test the limits of computer systems. Others saw it as a form of playful rebellion or a way to express frustration. The motivations varied, but they consistently reflected the technological landscape and societal attitudes of the time.
The Development of Anti-Virus Software: History Of Cybersecurity And Computer Viruses
Source: co.uk
The rapid proliferation of computer viruses in the late 1980s and early 1990s spurred the urgent need for countermeasures. Early responses to this escalating threat were largely reactive and focused on identifying and removing known infections. This nascent field of antivirus software development required a blend of technical ingenuity and a deep understanding of how these malicious programs operated.The initial antivirus programs were rudimentary compared to their modern counterparts.
They relied heavily on signature-based detection, which involved identifying specific patterns of code within a file to recognize a virus. This approach, while effective for known threats, was severely limited in its ability to detect novel or polymorphic viruses.
Early Antivirus Programs and Limitations
The development of the first antivirus programs was driven by the increasing prevalence of computer viruses. Early solutions were largely reactive, focused on identifying and removing known viruses rather than proactively preventing infections. These early programs often employed simple scanning techniques to search for specific virus signatures.These early programs were limited in their effectiveness. They were largely reliant on a database of known virus signatures, making them vulnerable to new and unknown viruses.
Furthermore, their detection capabilities were often limited to the specific viruses included in their databases. Consequently, these early antivirus programs were not capable of handling sophisticated or polymorphic viruses, which could alter their code to evade detection.
Key Principles and Techniques in Early Antivirus Software
Early antivirus software primarily relied on signature-based detection. This involved identifying specific patterns of code or byte sequences within a file that were characteristic of a known virus. Another technique was heuristic analysis, which involved examining the program’s behavior rather than its code. This approach could detect viruses that had not yet been identified, but it was less reliable and could lead to false positives.
Timeline of Antivirus Software Evolution
The evolution of antivirus software can be tracked through key advancements in detection and prevention methods.
- 1980s-1990s: The initial antivirus programs emerged, primarily using signature-based detection to identify known viruses. These early tools were limited by the lack of comprehensive virus databases and the ability of viruses to mutate. Examples include the first versions of Dr. Web and McAfee.
- Late 1990s-2000s: Heuristic analysis and behavioral monitoring techniques were integrated into antivirus programs. This allowed for the detection of previously unknown viruses based on their behavior rather than their specific code. The sophistication of viruses also increased, leading to more advanced detection algorithms. This period saw the rise of companies like Norton and Sophos, and a substantial increase in the number of users.
- 2000s-Present: Antivirus software has become increasingly sophisticated, with the integration of machine learning and artificial intelligence. These advanced technologies allow for the detection of sophisticated malware and threats, and for the proactive identification of potential vulnerabilities in computer systems. Cloud-based antivirus solutions further enhance the ability to quickly identify and respond to emerging threats.
Influence of Early Antivirus Techniques on Modern Approaches
The foundational techniques of early antivirus software, particularly signature-based detection and heuristic analysis, remain cornerstones of modern approaches. While modern antivirus software utilizes advanced technologies such as machine learning and cloud-based threat intelligence, the fundamental principles of identifying malicious code patterns and analyzing program behavior are still essential for effective virus detection and prevention. Early techniques laid the groundwork for the development of the sophisticated systems used today to protect against increasingly complex cyber threats.
Cybersecurity in the Internet Age
The advent of the internet revolutionized communication and information access, but it also ushered in a new era of cybersecurity challenges. The interconnected nature of the digital world created unprecedented opportunities for both collaboration and malicious activity, necessitating a paradigm shift in how we approach security. This transformation saw the rise of new threats, vulnerabilities, and sophisticated attack methods.The internet’s interconnectedness amplified the potential for harm.
A single compromised system could potentially expose an entire network, creating a cascading effect. This vulnerability became a fertile ground for cybercriminals to exploit, leading to a dramatic increase in the sophistication and frequency of attacks.
Emergence of Internet-Based Threats
The internet’s vast network offered new avenues for attackers. Phishing scams, distributed denial-of-service (DDoS) attacks, and malware designed to exploit vulnerabilities in internet protocols became prevalent. These threats posed a significant risk to individuals, organizations, and even critical infrastructure. For instance, the infamous MyDoom worm, a highly successful virus in the early 2000s, leveraged the internet to rapidly spread, infecting millions of computers worldwide.
Shift in Attack Methods and Cybercrime
Attack methods evolved from simple script kiddie activities to highly sophisticated, targeted attacks by organized criminal groups. Cybercrime became a lucrative business, with criminals targeting financial institutions, government agencies, and corporations for financial gain. Ransomware attacks, where hackers encrypt data and demand payment for its release, have become a significant concern. The notorious WannaCry ransomware attack, which impacted hospitals and other critical services, demonstrated the potential for significant disruption and harm.
Key Actors and Motivations
Cyberattacks are carried out by a diverse range of actors. These include state-sponsored groups seeking intelligence or disruption, hacktivists driven by ideological goals, and financially motivated criminals. Motivations range from espionage to profit to political agendas. The Stuxnet worm, a sophisticated piece of malware attributed to a joint U.S.-Israeli operation, exemplifies the use of cyberattacks for strategic purposes.
Comparison of Cybersecurity Challenges
| Characteristic | Pre-Internet Era | Internet Era |
|---|---|---|
| Attack Vectors | Limited to physical access, localized networks | Global networks, diverse attack vectors (e.g., phishing, DDoS) |
| Attack Sophistication | Generally less sophisticated, relying on basic techniques | Highly sophisticated, leveraging advanced tools and techniques |
| Attack Frequency | Relatively low | High, due to interconnectedness and ease of access |
| Impact | Localized | Potentially global and widespread |
| Motivations | Often personal or ideological | Often financial, political, or strategic |
The Evolution of Security Protocols and Standards
The proliferation of internet-based threats necessitates a constant evolution of security protocols and standards. Early defenses often proved inadequate against sophisticated attacks, prompting a continuous refinement of techniques and frameworks. This evolution is a crucial aspect of maintaining the integrity and security of digital systems in the face of ever-changing cyber landscapes.The development of robust security protocols and standards is a critical response to the escalating sophistication of cyber threats.
These standards not only safeguard individual users but also protect critical infrastructure and national security. The ongoing development and refinement of these protocols reflect a commitment to addressing the evolving nature of cyber threats and maintaining a secure digital environment.
Key Security Protocols
Various security protocols have been developed to address the diverse range of internet-based threats. These protocols form the bedrock of modern cybersecurity, enabling secure communication and data exchange. Their development is an ongoing process, constantly adapting to new vulnerabilities and attack vectors.
- SSL/TLS (Secure Sockets Layer/Transport Layer Security): SSL/TLS is a widely used protocol for securing communication over the internet. It establishes an encrypted channel between a client (like a web browser) and a server (like a web server), ensuring that data exchanged between them remains confidential and prevents eavesdropping. Its importance lies in protecting sensitive information transmitted online, such as login credentials, financial data, and personal information.
- IPsec (Internet Protocol Security): IPsec is a suite of protocols designed to provide secure communication at the network layer. It secures data packets as they travel across the internet, offering protection against unauthorized access and modification. Its use is often seen in virtual private networks (VPNs) and other secure network connections.
- SSH (Secure Shell): SSH provides a secure way to access remote servers and devices. It establishes an encrypted connection, preventing unauthorized access and ensuring that sensitive commands and data are transmitted securely. Its importance is particularly relevant in managing and administering systems remotely.
Role of Organizations like NIST
Organizations like the National Institute of Standards and Technology (NIST) play a pivotal role in establishing security standards. NIST develops and publishes guidelines, frameworks, and best practices that help organizations implement secure systems and practices. Their role is crucial in promoting interoperability and consistency in security measures across different systems and sectors.
- NIST Cybersecurity Framework: This framework provides a comprehensive approach to managing cybersecurity risk. It Artikels a structured process for identifying, assessing, and managing cybersecurity risks, which organizations can adapt to their specific needs and circumstances. This framework fosters a more standardized approach to cybersecurity, facilitating better coordination and collaboration among different entities.
Comparison of Security Protocols
Different security protocols have varying strengths and weaknesses. The choice of protocol depends on the specific security requirements and the nature of the data being protected.
| Protocol | Strengths | Weaknesses |
|---|---|---|
| SSL/TLS | Widely deployed, strong encryption, supports various applications. | Can be vulnerable to man-in-the-middle attacks if not properly configured. |
| IPsec | Provides strong protection at the network layer, supports VPNs. | Can be more complex to implement compared to SSL/TLS. |
| SSH | Secure remote access, strong authentication mechanisms. | Primarily focused on remote access, not suitable for all security needs. |
Encryption Techniques
Encryption techniques are fundamental to cybersecurity. They transform data into an unreadable format, making it inaccessible to unauthorized parties. Their role is crucial in protecting sensitive information from interception and misuse.
- Symmetric-key encryption: Uses the same key for encryption and decryption, offering speed but requiring secure key exchange. Examples include AES (Advanced Encryption Standard).
- Asymmetric-key encryption: Uses a pair of keys (public and private), allowing secure communication without prior key exchange. Examples include RSA (Rivest-Shamir-Adleman). This method is crucial for securing sensitive information exchanges where prior key exchange is impractical.
Sophisticated Attacks and Advanced Persistent Threats
The evolution of cybersecurity has seen a shift from simple malware infections to highly sophisticated attacks aimed at infiltrating networks and exfiltrating sensitive data. These advanced persistent threats (APTs) represent a significant challenge to organizations of all sizes, demanding proactive defense strategies and advanced threat intelligence.Advanced persistent threats are characterized by their stealthy nature, often operating undetected for extended periods.
These attacks exploit vulnerabilities in systems and networks to gain persistent access, enabling attackers to move laterally within the network and gain access to critical data and systems. The motivation behind these attacks can vary, ranging from financial gain to espionage or political sabotage. Understanding these threats and their tactics is crucial for developing effective defenses.
Evolution of Sophisticated Attacks
APT attacks have evolved significantly over time, becoming more complex and difficult to detect. Early attacks often relied on exploiting known vulnerabilities, while modern attacks frequently involve zero-day exploits, polymorphic malware, and advanced social engineering techniques. This evolution reflects the continuous arms race between attackers and defenders, where attackers constantly refine their methods and defenders must adapt their defenses accordingly.
Tactics, Techniques, and Procedures (TTPs)
APT attacks employ a wide range of tactics, techniques, and procedures (TTPs). These methods are meticulously planned and often involve multiple stages, each designed to evade detection and achieve the attacker’s objectives.
- Exploiting vulnerabilities: Attackers leverage known and unknown vulnerabilities in software and hardware to gain initial access. This often involves sophisticated penetration testing techniques and the creation of custom exploits.
- Social engineering: Manipulating individuals into divulging sensitive information or granting unauthorized access is a common tactic. This includes phishing campaigns, spear phishing targeting specific individuals, and pretexting to create trust and gain access to systems.
- Malware development: Advanced malware, often designed to evade detection by antivirus software, is frequently used. This includes polymorphic malware that changes its structure to avoid signature-based detection, and rootkits that conceal their presence within the operating system.
- Lateral movement: After initial access, attackers move laterally within the network to gain access to other systems and sensitive data. This often involves exploiting network configurations and privileges.
- Data exfiltration: The final stage involves exfiltrating the collected data, often using encrypted channels or techniques to conceal the data transfer. This is a crucial element to the attackers’ success.
Motivations Behind Sophisticated Attacks
The motivations behind sophisticated attacks vary greatly, often driven by strategic, financial, or ideological objectives.
- Espionage: Gathering intelligence about competitors, governments, or organizations is a primary motivation for many APTs. This involves stealing trade secrets, intellectual property, or other sensitive information.
- Financial gain: Financial motivations, such as stealing money or accessing financial accounts, are also common. This can involve targeting financial institutions, individuals, or businesses.
- Political sabotage: Disrupting critical infrastructure or spreading misinformation is another motivation. This can involve attacks on government agencies, media outlets, or other organizations.
- Hacktivism: Demonstrating political or social viewpoints through cyberattacks is another motivation, often involving disrupting services or websites.
Differences from Earlier Malware
Sophisticated attacks differ significantly from earlier forms of malware in their sophistication, persistence, and targeted nature. Early malware often had limited objectives and a broad impact. APTs, on the other hand, are meticulously planned and targeted at specific organizations or individuals, often with a longer-term goal. They also employ advanced evasion techniques and are designed to persist for extended periods.
Characteristics of Advanced Attacks
| Type of Attack | Characteristics |
|---|---|
| Advanced Persistent Threat (APT) | Highly sophisticated, targeted, persistent, and often involve multiple stages. |
| Ransomware | Designed to encrypt data and demand a ransom for its release. Often delivered through social engineering or exploiting vulnerabilities. |
| Malware | General term for malicious software. Earlier forms were less sophisticated and less targeted. |
| Phishing | A social engineering technique to trick individuals into revealing sensitive information. |
The Role of Data Breaches and Privacy Concerns
Data breaches have become increasingly prevalent and impactful in the digital age, significantly impacting individuals and organizations. The increasing interconnectedness of systems and the exponential growth of data volumes have created a fertile ground for malicious actors to exploit vulnerabilities. This necessitates a comprehensive understanding of data security and privacy, and the evolving regulatory landscape surrounding these critical issues.The frequency and severity of data breaches underscore the urgent need for robust security measures and a proactive approach to data protection.
Data breaches can result in the loss of sensitive information, financial losses, reputational damage, and legal repercussions. The evolving nature of these attacks requires a dynamic approach to cybersecurity strategies.
Impact of Data Breaches on Individuals
Data breaches can have severe consequences for individuals. Stolen personal information can be used for identity theft, leading to financial losses, credit damage, and emotional distress. Breaches can also expose individuals to scams, harassment, and other forms of malicious activity. The psychological impact of such breaches can be significant, leading to anxiety and a loss of trust in online services.
Impact of Data Breaches on Organizations
Organizations face significant financial, reputational, and operational risks from data breaches. Direct costs can include notification expenses, forensic investigations, and legal fees. Indirect costs, such as lost revenue, customer churn, and regulatory penalties, can be even more substantial. Data breaches can damage an organization’s reputation, eroding public trust and impacting its ability to attract and retain customers.
Evolving Regulatory Landscape
The regulatory landscape surrounding data privacy and security is constantly evolving. Regulations like GDPR (General Data Protection Regulation) in Europe and similar laws in other jurisdictions establish stringent requirements for data handling, emphasizing transparency, consent, and data subject rights. These regulations create a more secure environment, but the complexity and evolving nature of these laws demand ongoing adaptation by organizations.
Examples of Major Data Breaches and Their Consequences
Numerous high-profile data breaches have highlighted the devastating consequences of inadequate security measures. The 2017 Equifax breach, for example, exposed the personal information of over 147 million Americans, leading to significant financial and reputational damage for the company. The impact extended to individuals affected by the breach, who faced the prospect of identity theft and financial exploitation. Similarly, the 2018 Cambridge Analytica scandal demonstrated the vulnerability of personal data in the hands of third-party vendors.
These events underscore the critical need for strong security measures and adherence to privacy regulations. The consequences of a data breach are far-reaching and necessitate a thorough understanding of the impact on individuals and organizations.
Future Trends in Cybersecurity
Source: uscybersecurity.net
The landscape of cybersecurity is constantly evolving, driven by technological advancements and the ever-increasing sophistication of cyberattacks. Predicting the future of cybersecurity is challenging, but understanding emerging trends and their potential impacts is crucial for developing proactive defense strategies. This exploration examines key future trends, focusing on emerging technologies, the role of AI, and the importance of user education.The future of cybersecurity will be heavily influenced by emerging technologies, such as the rise of the Internet of Things (IoT) and the increasing reliance on cloud computing.
These advancements present both opportunities and challenges. Securely managing the vast network of interconnected devices in IoT environments is paramount, as is ensuring the integrity and confidentiality of data stored in cloud platforms. Simultaneously, new vulnerabilities and attack vectors will likely emerge, necessitating constant adaptation and innovation in security measures.
Emerging Technologies and Their Impact
The proliferation of IoT devices introduces a significant security concern. These devices, often lacking robust security features, create a vast attack surface. Simultaneously, the increasing reliance on cloud computing necessitates robust security measures to protect data stored and processed in cloud environments. The distributed nature of cloud infrastructure requires innovative approaches to access control and data encryption to prevent unauthorized access.
The Role of Artificial Intelligence and Machine Learning
AI and machine learning (ML) are transforming the cybersecurity landscape. AI-powered tools can analyze vast datasets to identify patterns and anomalies indicative of malicious activity. Machine learning algorithms can also be used to detect and respond to evolving threats, adapting to new attacks in real time. However, AI in cybersecurity also presents challenges. Adversaries can also leverage AI to develop more sophisticated attacks.
User Education and Awareness
User education and awareness remain critical components of a robust cybersecurity posture. Educating users about common security threats, such as phishing scams and social engineering tactics, is essential to mitigate the risk of human error. This includes providing training on identifying suspicious emails, recognizing malicious websites, and implementing strong passwords. Cybersecurity awareness programs are not a one-time event; ongoing training and reinforcement are necessary to ensure users remain vigilant.
The Potential of Quantum Computing
Quantum computing holds the potential to revolutionize both cybersecurity and cyberattacks. The unique capabilities of quantum computers could break existing encryption algorithms, rendering current security systems vulnerable. This poses a significant threat to data confidentiality and integrity. Consequently, research and development in post-quantum cryptography are critical to maintaining security in the face of quantum computing’s potential impact.
This necessitates the development of new encryption algorithms that are resistant to attacks by quantum computers. The transition to these new algorithms is likely to be gradual and complex.
Conclusive Thoughts
In conclusion, the history of cybersecurity and computer viruses is a compelling story of constant adaptation. From the early days of computing to the complexities of the modern digital age, the struggle against malicious code has shaped the technologies we use today. The lessons learned from past threats inform our strategies for future challenges, ensuring that we remain vigilant against emerging cyber threats.












Post Comment