Common Ways Computers Get Infected With Viruses
Common ways computers get infected with viruses, from phishing scams to exploiting network weaknesses, are explored in detail. Understanding these methods is crucial for protecting your systems from malicious attacks. This comprehensive guide examines various infection vectors, malicious software delivery methods, and vulnerabilities in software and systems.
This exploration delves into the tactics employed by cybercriminals, including phishing techniques, social engineering strategies, and the analysis of malicious code. We will also look at the impact of infections on individuals and businesses, and highlight the importance of proactive security measures.
Infection Vectors
Computer viruses and malware infiltrate systems through various avenues, often exploiting vulnerabilities in software or user behavior. Understanding these vectors is crucial for implementing robust security measures. Recognizing the methods of attack allows for proactive defenses against infection.
Common Infection Vectors
Infection vectors are the pathways through which malicious software gains access to a system. These pathways can be categorized into several common methods, each with unique characteristics. A comprehensive understanding of these vectors is vital to mitigating risks.
- Email Attachments: Malicious code often masquerades as legitimate files, such as documents or images. Users unknowingly open these attachments, triggering the infection process. Phishing emails frequently use this tactic, tricking recipients into downloading and running harmful files.
- Malicious Websites: Visiting compromised websites can expose systems to malware. These websites may host malicious scripts or downloads that infect the visitor’s machine. Exploits in browser vulnerabilities or drive-by downloads can compromise systems without user interaction.
- Software Downloads: Malicious software can be disguised as legitimate software, often from untrusted sources. Users downloading and installing software from unreliable websites can inadvertently install viruses.
- USB Drives: Infected USB drives can spread malware when connected to a susceptible system. The drive may contain hidden malicious code that automatically executes upon connection. This vector is particularly dangerous in shared work environments.
- Social Engineering: Sophisticated tactics like phishing, pretexting, and baiting exploit human psychology. Malicious actors attempt to trick users into divulging sensitive information or executing actions that compromise their systems.
- Exploiting Vulnerabilities in Existing Software: Outdated or poorly secured software often contains vulnerabilities that malicious actors can exploit. These vulnerabilities allow malware to bypass security measures and gain unauthorized access.
Types of Malicious Software
Various types of malicious software exploit different infection vectors. Knowing these types is important for understanding the potential consequences of each infection vector.
- Viruses: Viruses are self-replicating programs that attach themselves to other files. They spread by infecting other files or programs on the system.
- Worms: Worms are independent programs that spread autonomously through networks. They often exploit security holes in network protocols.
- Trojan Horses: Trojan horses are disguised as legitimate programs but contain malicious code. They can install additional malware or steal sensitive data once executed.
- Ransomware: Ransomware encrypts files and demands payment for their release. This type of malware can cripple systems and cause significant financial losses.
- Spyware: Spyware monitors user activity and collects sensitive information, such as keystrokes and browsing history. This information can be used for identity theft or financial fraud.
Vulnerabilities Exploited by Infection Vectors
Infection vectors exploit specific vulnerabilities in computer systems. Understanding these vulnerabilities helps develop robust security strategies.
| Vector Type | Examples of Software | Vulnerability Exploited |
|---|---|---|
| Email Attachments | Microsoft Word documents, PDF files | Buffer overflows, code execution vulnerabilities in software |
| Malicious Websites | Compromised websites, malicious ads | Cross-site scripting (XSS), SQL injection, and other vulnerabilities in web applications |
| Software Downloads | Fake antivirus software, cracked software | Lack of code validation, insufficient input sanitization |
| USB Drives | Infected USB drives | Lack of proper security checks, auto-execution of scripts |
| Social Engineering | Phishing emails, fake websites | Human error, lack of security awareness |
| Exploiting Vulnerabilities in Existing Software | Outdated operating systems, browsers, and applications | Unpatched security vulnerabilities, buffer overflows, remote code execution |
Phishing and Social Engineering

Source: informationq.com
Phishing and social engineering are sophisticated methods employed by malicious actors to manipulate individuals into divulging sensitive information or installing malware on their systems. These tactics often exploit human psychology and trust, making them effective even against well-meaning users. Understanding the tactics and examples of these attacks is crucial for bolstering user defenses.Phishing attacks leverage deception to trick individuals into revealing personal information, such as usernames, passwords, credit card details, or social security numbers.
This information is then used for fraudulent activities or to gain unauthorized access to accounts. Social engineering campaigns, on the other hand, focus on manipulating human behavior to achieve a desired outcome. They prey on trust, fear, curiosity, and other emotional vulnerabilities. Both methods can result in significant harm, including financial losses, identity theft, and compromised computer systems.
Phishing Tactics
Phishing attacks often mimic legitimate communications, such as emails, messages, or websites. The goal is to trick the recipient into clicking a malicious link or opening a malicious attachment. These attacks employ various techniques to achieve their goals, such as impersonating trusted entities, creating a sense of urgency, and exploiting personal information.
Examples of Deceptive Communications
Phishing attacks often employ deceptive emails, messages, and websites to trick users. These communications often mimic trusted entities, such as banks, social media platforms, or government agencies. They use alarming subject lines and content to instill a sense of urgency or fear, urging immediate action. These attacks may request sensitive information, such as login credentials, or direct users to malicious websites that appear legitimate.
Psychological Manipulation in Social Engineering
Social engineering campaigns utilize psychological manipulation techniques to exploit human vulnerabilities. These techniques are often subtle and persuasive, playing on emotions and trust to achieve the attacker’s goals. Common tactics include impersonation, creating a sense of urgency, and leveraging social proof. By understanding these techniques, individuals can be better prepared to recognize and avoid social engineering attempts.
User Awareness Training
User awareness training plays a critical role in mitigating social engineering attacks. Such training equips users with the knowledge and skills to identify and avoid phishing attempts and social engineering tactics. This training helps individuals recognize suspicious emails, messages, and websites. By understanding the common tactics used in these attacks, users can become more discerning and less susceptible to manipulation.
Common Phishing Email Subject Lines and Deceptive Content
| Subject Line | Deceptive Content |
|---|---|
| Urgent Account Action Required | An email claiming an account needs immediate attention, often threatening account suspension or closure if action is not taken. The email typically directs users to a fake website. |
| Important Security Update | A message that informs the recipient of a security breach or an urgent security update requiring immediate action. The email often contains a link to a fake website. |
| Shipping Confirmation | A message falsely claiming a package is awaiting delivery, requiring the recipient to click on a link to track it. The link usually leads to a malicious website. |
Malicious Software Delivery Methods
Malicious software, often referred to as malware, isn’t magically implanted into systems. It needs a pathway, a method of entry. Understanding these delivery methods is crucial for preventing infections. Various tactics are employed by attackers, ranging from seemingly innocuous downloads to sophisticated social engineering schemes.Various methods exist for introducing malware, each with its own characteristics and effectiveness.
These methods exploit vulnerabilities in software, operating systems, or human behavior to achieve their objectives. A deep understanding of these methods is vital for both individual users and organizations seeking to mitigate the risk of malware infections.
Common Delivery Methods
A variety of channels are used to distribute malicious software. These channels exploit different weaknesses and rely on varying levels of user interaction. Some are more subtle than others, making them harder to detect.
- Malicious Websites: These websites may appear legitimate but contain embedded malware. Visiting these sites can lead to the download of malicious files or the execution of scripts that install malware without the user’s knowledge. Attackers often disguise these sites to mimic legitimate resources, making them convincing traps for unsuspecting victims. This method leverages the user’s trust in legitimate websites and exploits the human tendency to click on links without careful consideration.
- Malicious Downloads: Malicious software can be disguised as legitimate software, such as a game or a utility. These files may be offered for free or bundled with other downloads, potentially infecting the user’s system upon installation. Users may unknowingly download and execute these files from untrusted sources, such as peer-to-peer file-sharing networks or unofficial websites. The common characteristic is the deception and trust-exploitation of the user.
- Removable Media: Infected USB drives, CDs, or DVDs can spread malware when inserted into a computer. This method relies on the user’s curiosity or the need to transfer data to potentially infected media. The infection occurs when the user interacts with the media, often without recognizing the risk.
Effectiveness Comparison
The effectiveness of different delivery methods varies based on several factors, including the sophistication of the attack, the target audience, and the prevalence of security measures in place.
| Delivery Method | Success Rate (Estimated) | User Interaction Required |
|---|---|---|
| Malicious Websites | High, especially for less security-aware users. | Minimal (often just visiting the website). |
| Malicious Downloads | Moderate, depending on the sophistication of the disguise. | Moderate (downloading and potentially installing software). |
| Removable Media | Low, but possible with targeted attacks. | High (inserting and potentially interacting with the media). |
Examples of Malware Delivery
- Malicious Websites: A seemingly legitimate software download site may host malicious code. Users downloading a file from the site may unknowingly install a keylogger, which records their keystrokes.
- Malicious Downloads: A freeware program masquerading as a utility may contain malware. Users installing the program could compromise their system with ransomware. This can lead to the encryption of critical data, requiring a ransom to be paid for decryption.
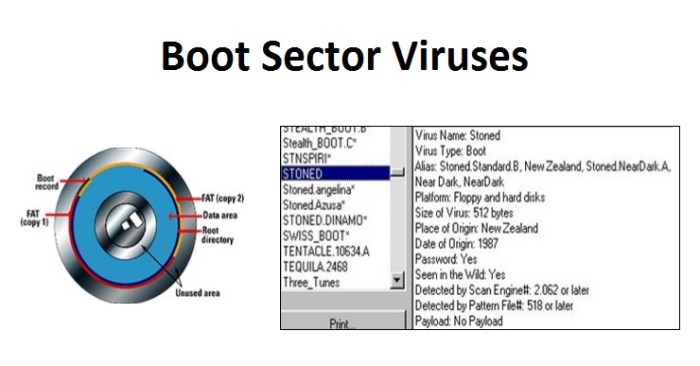
- Removable Media: A seemingly innocuous USB drive left in a public place might contain a boot sector virus. A user inserting the drive into their computer could cause the virus to execute on startup, potentially infecting the entire system.
Vulnerabilities in Software and Systems
Software and systems are often riddled with vulnerabilities, which malicious actors can exploit to gain unauthorized access and install viruses. These vulnerabilities can stem from various sources, including flawed coding practices, outdated components, and inadequate security configurations. Understanding these vulnerabilities is crucial for bolstering system defenses and mitigating the risk of infection.
Common Software Vulnerabilities
Software, in its inherent complexity, can contain weaknesses that attackers leverage. These vulnerabilities, if left unpatched, can lead to serious security breaches. Examples include buffer overflows, where attackers exploit a program’s inability to handle large amounts of data, leading to code execution; SQL injection attacks, where malicious SQL code is inserted into a database query, potentially revealing sensitive data or granting unauthorized access; and cross-site scripting (XSS) vulnerabilities, where attackers inject malicious scripts into websites to steal user data or hijack sessions.
Each of these vulnerabilities, when exploited, can lead to significant security consequences.
Role of Outdated Software and Operating Systems
Outdated software and operating systems are often significantly more vulnerable to attacks. Patches and updates frequently address known security flaws. Leaving systems unpatched exposes them to known exploits, increasing the risk of infection. The lack of timely updates can make systems susceptible to malware that exploits previously fixed vulnerabilities. The longer a system remains unpatched, the more likely it is to become a target.
For instance, a widely used operating system without security updates could be susceptible to a newly discovered exploit, exposing countless users to potential threats.
Security Misconfigurations
Inadequate security configurations significantly increase the risk of computer infections. Incorrectly configured firewalls, weak passwords, or open ports can all serve as entry points for malicious actors. Improper access controls and insufficient logging mechanisms further complicate the detection and response to security incidents. For instance, a web server with insecure default settings could easily be exploited by attackers.
Vulnerabilities in Web Browsers, Plugins, and Applications
Web browsers, plugins, and applications are common targets for attackers due to their frequent interaction with potentially malicious websites and files. Security flaws in these components can allow attackers to execute malicious code on the user’s system. For example, a browser vulnerability could enable the execution of malicious code when a user visits a compromised website, leading to the installation of malware.
Likewise, vulnerabilities in plugins or applications can allow attackers to gain unauthorized access or execute malicious code. This can result in various detrimental consequences, from data theft to system compromise.
Software Vulnerability Impact
| Vulnerability | Description | Impact on System |
|---|---|---|
| Buffer Overflow | A program attempts to write more data to a buffer than it can hold. | Potential for code execution, system crashes, or unauthorized access. |
| SQL Injection | Malicious SQL code is inserted into a database query. | Data breaches, unauthorized access to sensitive information, and database corruption. |
| Cross-Site Scripting (XSS) | Attackers inject malicious scripts into websites. | Data theft, session hijacking, and potentially installation of malware. |
| Cross-Site Request Forgery (CSRF) | Attackers trick users into performing unwanted actions on a website. | Unauthorized actions, data breaches, and potential system compromise. |
| Remote File Inclusion (RFI) | Attackers include a remote file in a web application. | Malicious code execution, data breaches, and system compromise. |
Exploiting Network Weaknesses
Network vulnerabilities represent a significant vector for computer infections. Attackers frequently exploit these weaknesses to gain unauthorized access and deploy malicious software. Understanding how these exploits work is crucial for implementing effective preventative measures. A compromised network can have devastating consequences, impacting data integrity, confidentiality, and availability.Network security is a multifaceted domain. Protecting against exploits requires a layered approach, combining robust security measures with the ongoing monitoring and patching of systems.
This includes understanding the intricacies of network protocols, identifying potential vulnerabilities, and implementing countermeasures.
Unpatched Network Devices
Unpatched network devices are prime targets for attackers. These devices, often overlooked in security assessments, harbor vulnerabilities that can be exploited to gain access to the entire network. A single compromised device can act as a springboard for further attacks, potentially leading to widespread infections. This emphasizes the importance of regular security updates and patches for all network components, including routers, switches, firewalls, and servers.
Vulnerable Network Protocols and Services
Numerous network protocols and services are susceptible to attacks. These vulnerabilities can stem from flaws in the protocol’s design or implementation, or from the way the service is configured. Common targets include vulnerable versions of protocols like FTP, Telnet, and SMB. Also, poorly secured web servers, databases, and email servers are frequent targets, often exposed to exploits through inadequate configuration or outdated software.
Misconfigured network services, if left unaddressed, pose a considerable security risk.
Network Security Measures
Effective network security measures are essential to prevent infections. These measures include robust firewalls, intrusion detection systems (IDS), and intrusion prevention systems (IPS). Regular security audits, vulnerability assessments, and penetration testing can help identify and address potential vulnerabilities before they are exploited. Implementing strong access controls, including user authentication and authorization, further limits the potential impact of a breach.
Comparison of Network Vulnerabilities and Countermeasures
| Network Vulnerability | Description | Countermeasure |
|---|---|---|
| Outdated Operating Systems | Legacy operating systems often lack crucial security patches, making them vulnerable to known exploits. | Regularly update operating systems and software to the latest versions. |
| Unpatched Network Devices | Routers, switches, and other network infrastructure components with unapplied security patches are susceptible to exploitation. | Implement a system for regular patching and updates for all network devices. |
| Weak Passwords | Easily guessed or predictable passwords provide unauthorized access to network resources. | Implement strong password policies requiring complex and unique passwords. |
| Misconfigured Firewalls | Improperly configured firewalls can leave critical ports and services open to attacks. | Regularly review and update firewall configurations to block unauthorized access. |
| Phishing Attacks Targeting Network Credentials | Phishing attempts to trick users into revealing their network credentials, leading to unauthorized access. | Educate users about phishing tactics and implement robust email security measures. |
Malicious Code Analysis
Malicious code, often referred to as malware, encompasses a wide range of harmful programs designed to infiltrate and compromise computer systems. Understanding the various types, their methods of operation, and the stages of their execution is crucial for effective defense strategies. This analysis will explore the characteristics of different malware types, their infection mechanisms, and the tactics employed by attackers to evade detection.Different types of malicious code exhibit unique characteristics and behaviors.
Their primary goal, however, remains the same: to exploit vulnerabilities and cause harm. This involves manipulating data, stealing information, or disrupting system functionality. These malicious actions can have significant repercussions for individuals, organizations, and the broader digital ecosystem.
Types of Malicious Code, Common ways computers get infected with viruses
Malicious code manifests in various forms, each with distinct characteristics and purposes. These range from simple viruses to complex sophisticated threats. Key types include:
- Viruses: Viruses are self-replicating programs that attach themselves to legitimate files. They typically spread through file sharing, email attachments, and infected websites. Their primary objective is replication, often disrupting system functionality in the process.
- Worms: Worms are independent programs that exploit security vulnerabilities to spread across networks. Unlike viruses, they do not need to attach themselves to existing files. They can rapidly propagate through networks, often causing significant network congestion and bandwidth depletion.
- Trojans: Trojans masquerade as legitimate software. Upon execution, they install malicious code on the system, often granting unauthorized access to attackers. Unlike viruses, Trojans do not self-replicate.
- Ransomware: Ransomware encrypts files on a victim’s system and demands payment in exchange for the decryption key. This type of malware can cripple businesses and individuals by locking out access to critical data.
- Spyware: Spyware monitors user activity without their knowledge or consent. It collects sensitive information like login credentials, browsing history, and keystrokes, often transmitting this data to a remote attacker.
Virus Operation on a Computer System
Viruses operate by exploiting vulnerabilities in a computer system. They use various techniques to propagate and execute their malicious code.
- Infection Mechanisms: Viruses can infect files, boot sectors, or system memory. They often attach themselves to executable files, scripts, or documents, waiting for the host file to be executed to trigger the virus’s malicious code.
- Replication: The virus’s ability to replicate itself is crucial to its spread. It copies itself to other files or systems, ensuring its continued presence and potential for further damage.
- Execution: Once a virus is activated, it executes its malicious code, potentially damaging files, deleting data, or altering system configurations.
Stages of Virus Execution
The execution of a virus typically involves distinct stages:
- Infection: The virus infects a host file or system, embedding its code within it.
- Replication: The virus copies itself to other files or systems, spreading its presence.
- Activation: The virus waits for a trigger event, such as a specific date, time, or user action.
- Execution: Upon activation, the virus executes its malicious code.
- Dissemination: The virus spreads further, potentially affecting other systems and users.
Methods to Evade Detection
Malware authors employ various techniques to evade detection by antivirus software:
- Polymorphism: Modifying the virus’s code structure to avoid signature-based detection. This makes it difficult for antivirus software to identify the virus.
- Metamorphism: Transforming the virus’s code at runtime to avoid detection. This technique makes it even more difficult to identify the virus compared to polymorphism.
- Rootkits: These tools hide malicious code or processes from operating systems. This enables attackers to remain undetected and maintain persistent access to compromised systems.
- Obfuscation: Making the virus code more difficult to understand or analyze by using techniques such as code compression or encryption. This makes it harder for researchers to reverse-engineer the malicious code and identify its functions.
Example of Malicious Code
// Example of a simple malicious code snippet (Illustrative purpose only) // This code is for educational purposes and should not be used for malicious activities. #include <iostream> #include <windows.h> int main() // Delete a specific file DeleteFile("C:\\important_file.txt"); std::cout << "File deleted successfully." << std::endl; return 0;
This example demonstrates a basic malicious code snippet that deletes a specific file. Real-world malicious code is significantly more complex and sophisticated. The snippet is provided to illustrate the concept and should not be executed in a production environment.
Impact of Infections
Source: informationq.com
Computer infections, regardless of their origin or sophistication, can have a profound and multifaceted impact on individuals and organizations. These repercussions extend beyond simple disruptions, often resulting in significant financial losses, reputational damage, and compromised user privacy. Understanding these consequences is crucial for developing robust security measures and mitigating the risks associated with malicious software.
Financial Consequences
The financial implications of computer infections can range from minor inconveniences to substantial losses. Direct costs include expenses related to data recovery, system restoration, and the potential need for new hardware or software. Indirect costs, often more substantial, encompass lost productivity, reduced efficiency, and the expense of legal and public relations interventions. For instance, a business experiencing a ransomware attack might face significant downtime, impacting revenue generation and customer satisfaction, while simultaneously incurring costs for ransom payment, data recovery, and system upgrades.
Reputational Damage
A compromised system can severely tarnish an organization’s reputation. Public disclosure of a security breach can lead to a loss of trust among customers, partners, and investors. Negative publicity can negatively impact brand perception and lead to a decline in sales. A prominent example is the case of a major retailer whose customer data was stolen, leading to significant reputational damage and a decline in consumer confidence.
Impact on User Privacy and Data Security
Infections can expose sensitive personal or corporate data, resulting in a severe violation of user privacy. Stolen credentials, compromised financial information, and leaked confidential documents can have devastating consequences for individuals and organizations. The risk of identity theft, financial fraud, and legal ramifications is considerable. For example, a user’s email account being compromised can expose their personal information, financial data, and passwords, creating significant risks for them.
Examples of Significant Harm
Numerous instances demonstrate the severe impact of infections. Large-scale ransomware attacks on critical infrastructure have caused widespread disruption and financial losses. Phishing campaigns have resulted in substantial financial losses for individuals and organizations. Furthermore, the theft of sensitive data, such as customer records or intellectual property, can have long-term consequences for the affected entities.
Scenario: Impact on a Business
Consider a small online retail business. A successful phishing campaign targets employees, gaining access to customer data and payment processing credentials. This compromise results in the theft of sensitive information and leads to significant financial losses from fraudulent transactions. The business experiences a sharp decline in customer trust and loyalty, leading to lost sales and potential legal action.
Furthermore, the reputation of the business is severely damaged, potentially making it difficult to attract future customers and investors. The business may also face regulatory penalties for failing to protect sensitive customer data.
End of Discussion: Common Ways Computers Get Infected With Viruses

Source: futurecdn.net
In conclusion, safeguarding your digital assets requires a multifaceted approach. Understanding the common pathways for virus infiltration, recognizing the methods used to deliver malicious software, and acknowledging vulnerabilities in software and systems is paramount. By understanding these elements, you can implement appropriate security measures to protect your devices and data. A strong foundation in cybersecurity knowledge is essential in today’s digital landscape.












Post Comment