Most Secure Programming Languages 2025
Most secure programming languages 2025 are crucial for building robust and trustworthy software. As cyber threats evolve, developers need languages equipped to handle vulnerabilities. This exploration delves into the key factors driving the need for secure programming languages, comparing leading contenders like Java, C#, Python, Go, and Rust, and examining emerging trends.
Understanding the strengths and weaknesses of different programming paradigms in a security context is essential. We’ll analyze common vulnerabilities and effective mitigation strategies, offering practical examples and real-world scenarios to illustrate the concepts. This comprehensive guide equips readers with the knowledge to make informed decisions about choosing the most secure programming languages for their projects in 2025.
Introduction to Secure Programming Languages
In 2025, secure programming practices are no longer a desirable add-on, but a fundamental requirement for software development. The increasing reliance on software in critical infrastructure, financial systems, and everyday devices necessitates robust security measures at the language level. This shift underscores the critical role of programming languages in mitigating vulnerabilities and building resilient applications.The need for robust security in software development stems from the ever-evolving threat landscape.
Sophisticated attacks are becoming more frequent and complex, targeting vulnerabilities in software applications to gain unauthorized access, manipulate data, or disrupt services. Consequently, the need for secure coding practices, which extends to the choice of programming languages, is paramount. The potential consequences of insecure software range from data breaches and financial losses to system disruptions and reputational damage.
Examples include the infamous Equifax breach, highlighting the devastating impact of exploitable vulnerabilities.
Common Vulnerabilities in Programming Languages
Programming languages, despite their inherent strengths, are susceptible to various vulnerabilities. These vulnerabilities, if not addressed, can lead to serious security breaches. Buffer overflows, SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF) are examples of common attacks that exploit flaws in programming languages. For instance, insufficient input validation can lead to buffer overflows, allowing attackers to execute arbitrary code.
SQL injection vulnerabilities arise when user-supplied data is not properly sanitized before being used in SQL queries.
Security Characteristics of Programming Language Paradigms
Different programming language paradigms exhibit varying security characteristics. The choice of paradigm directly impacts the likelihood of introducing vulnerabilities and the potential for mitigating them. This table compares common paradigms in terms of security considerations:
| Programming Paradigm | Security Characteristics | Example Vulnerabilities |
|---|---|---|
| Object-Oriented | Object-oriented languages often provide mechanisms for encapsulation and data hiding, which can enhance security by restricting direct access to sensitive data. However, complex inheritance hierarchies and dynamic dispatch can introduce vulnerabilities if not managed carefully. | Injection flaws, race conditions, and incorrect use of access modifiers. |
| Functional | Functional languages, by their nature, promote immutability and referential transparency, which can reduce the likelihood of certain types of vulnerabilities, such as those related to state-based attacks. However, concurrency issues can arise in functional programming paradigms that involve shared mutable state. | Concurrency vulnerabilities, unintended mutable state, race conditions. |
| Procedural | Procedural languages often rely on manual memory management and intricate control flow, making them susceptible to buffer overflows and other memory-related vulnerabilities. However, procedural programming can offer precise control over system resources. | Buffer overflows, pointer errors, format string vulnerabilities. |
Top Contenders for Most Secure Programming Languages
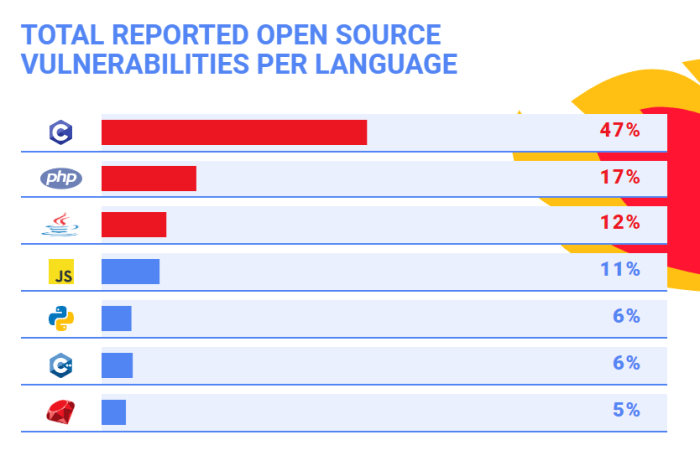
Source: technotification.com
Predicting the most secure programming languages in 2025 requires careful consideration of current trends and emerging threats. Security is not a static feature but an evolving aspect of software development. Languages that excel in verifiable security properties, memory management, and robust tooling are likely to hold a prominent position.The quest for secure software extends beyond language features. Strong developer training, secure coding practices, and rigorous testing methodologies are vital components of a robust security strategy.
The most secure language in 2025 will likely be a combination of inherent security characteristics and the supportive ecosystem surrounding its use.
Leading Programming Languages in Security
Several programming languages have demonstrated a strong track record in security, often due to their inherent design principles. Java, C#, Python, Go, and Rust are notable contenders. Their relative strengths and weaknesses in terms of security are complex and depend on the specific use case.
Security Features Comparison
| Language | Key Security Features | Example Code Snippets |
|---|---|---|
| Java | Strong typing, garbage collection, extensive libraries for security. The Java Virtual Machine (JVM) offers a level of security through sandboxing. Java has a large, mature ecosystem with established security practices. | “`java// Example demonstrating input validationString input = request.getParameter(“username”);if (input == null || input.length() < 3 || input.length() > 20) throw new IllegalArgumentException(“Invalid username”);“` |
| C# | Managed code, garbage collection, and a rich set of security features built into the .NET framework. C# integrates well with other security tools and frameworks. Strong type checking and automatic memory management mitigate vulnerabilities. | “`C#// Example demonstrating secure string handlingstring password = Request.Form[“password”];string hashedPassword = BCrypt.Net.BCrypt.HashPassword(password);“` |
| Python | Dynamic typing can lead to runtime errors, but strong libraries like cryptography and frameworks like Django offer significant security tools. Python’s readability and ease of use make it a popular choice for rapid development, which needs security considerations. | “`pythonimport hashlibdef hash_password(password): salt = hashlib.sha256(os.urandom(60)).hexdigest() hashed_password = hashlib.sha256(salt.encode() + password.encode()).hexdigest() return f”salt:hashed_password”“` |
| Go | Memory safety features, concurrency primitives designed with security in mind, and a focus on secure defaults. Go’s static typing, and emphasis on efficient code, contribute to security. | “`gopackage mainimport ( “fmt” “crypto/rand”)func main() // Example of secure random number generation var b [32]byte _, err := rand.Read(b[:]) if err != nil fmt.Println(“Error generating random number:”, err) fmt.Printf(“%x\n”, b)“` |
| Rust | Memory safety through ownership and borrowing systems, leading to fewer vulnerabilities. Rust’s focus on zero-cost abstractions and explicit memory management reduces runtime errors. This makes it a language of choice for performance-critical systems. | “`rustfn main() let mut data = String::from(“Hello”); data.push_str(” World!”); println!(“”, data);“` |
Strengths and Weaknesses of Each Language
Each language exhibits unique strengths and weaknesses regarding security. Java’s mature ecosystem provides a wealth of security libraries, while Python’s rapid development capabilities might come at the cost of security if proper practices are not followed. C# benefits from .NET’s extensive security framework, but its managed code nature can sometimes hide potential vulnerabilities. Go excels in concurrent programming with built-in security features, but developers need to be aware of potential race conditions.
Rust’s memory safety guarantees significantly reduce vulnerabilities but require a steeper learning curve. Careful consideration of the specific application and development team expertise is crucial in choosing the most secure language.
Security Features and Practices
Robust security in software development transcends mere code; it’s a holistic approach integrating best practices throughout the entire software lifecycle. A secure language, by itself, does not guarantee security. Development teams must adopt and rigorously implement secure coding techniques, which are often language-agnostic. This necessitates a deep understanding of vulnerabilities, appropriate mitigation strategies, and ongoing vigilance.Security in software development is a complex field.
Various techniques and best practices are crucial for building secure applications. Effective implementation of these practices often requires careful consideration of the specific programming language and the potential risks inherent in its use. This section will elaborate on common security best practices and how different languages address them.
Common Security Best Practices
Secure coding practices encompass a range of techniques aimed at minimizing vulnerabilities. These practices include, but are not limited to, secure input validation, robust memory management, and the avoidance of known coding errors. Properly implementing these practices helps reduce the attack surface of applications.
- Input Validation: This involves meticulously checking and sanitizing all user inputs before using them in the application. Failing to validate inputs can lead to vulnerabilities like SQL injection, cross-site scripting (XSS), and command injection, allowing malicious actors to manipulate the application’s behavior.
- Memory Safety: Languages with strong memory management systems, like those employing garbage collection, are less prone to memory-related vulnerabilities. Memory leaks, buffer overflows, and dangling pointers are critical vulnerabilities that can be mitigated with proper memory management.
- Secure Coding Techniques: This encompasses a wide array of practices, including avoiding common coding errors, employing secure libraries and frameworks, and adhering to established coding standards. Following secure coding standards helps developers avoid potential vulnerabilities, enhancing the overall security posture of the application.
Language Support for Security Best Practices
Different programming languages offer varying levels of support for secure coding practices. The degree of built-in safety and the required developer effort differ significantly.
- Python: Python’s dynamic typing and extensive libraries often facilitate rapid development but can pose challenges for static security analysis. However, Python’s libraries and frameworks offer built-in security features for handling inputs, like parameterized queries for database interactions, and support for secure string formatting.
- C++: C++’s low-level access to memory can lead to vulnerabilities like buffer overflows if not handled meticulously. However, C++ allows developers to manually control memory allocation and deallocation, enabling more intricate and fine-tuned security measures.
Examples of Secure Coding Practices
Illustrative examples showcasing secure coding practices in different languages can highlight the importance of adhering to specific security principles.
- Secure String Handling in Python: Using parameterized queries in database interactions is crucial. Avoid string concatenation when dealing with user inputs to prevent SQL injection vulnerabilities. Use the `str.format()` method or f-strings for safer string formatting.
- Memory Management in C++: Employ smart pointers like `unique_ptr` and `shared_ptr` to prevent memory leaks and dangling pointers. Avoid manual memory management whenever possible to reduce the risk of buffer overflows.
Security Vulnerabilities and Mitigation Strategies
A table summarizing common security vulnerabilities and mitigation strategies across different languages can offer a concise overview.
| Vulnerability | Description | Mitigation Strategies (Python) | Mitigation Strategies (C++) |
|---|---|---|---|
| SQL Injection | Malicious input manipulates SQL queries | Parameterized queries | Parameterized queries, prepared statements |
| Cross-Site Scripting (XSS) | Malicious script injected into a webpage | Input validation, output encoding | Input validation, output encoding |
| Buffer Overflow | Writing beyond allocated memory | Python’s dynamic typing mitigates this, but careful input validation is essential | Use smart pointers, avoid manual memory management |
Emerging Trends and Future of Secure Programming Languages
The landscape of programming languages is constantly evolving, driven by the ever-present need for robust and secure software. Emerging trends in secure programming language development are pushing the boundaries of vulnerability mitigation, focusing on proactive security measures integrated directly into the language’s design. This shift reflects a growing recognition that security should be a fundamental aspect of software development, not an afterthought.These advancements are not just theoretical; they are already influencing the design and implementation of new and existing programming languages.
This focus on security-by-design is transforming how developers approach software creation, promoting more secure and reliable applications.
Security-Focused Language Design
The evolution of programming languages towards enhanced security is not simply about adding new features. It’s a fundamental shift in how security is considered, integrating it into the core structure of the language itself. This proactive approach allows developers to write more secure code by default, reducing the risk of common vulnerabilities. Examples of this include incorporating type systems that detect potential errors early in the development process and designing memory management mechanisms that prevent memory corruption attacks.
Advanced Type Systems
Advanced type systems are gaining traction, allowing for stricter validation of data and code during compilation. These systems can identify and flag potential security vulnerabilities before runtime, leading to more secure applications. Languages like Rust and Swift are prime examples of this trend, leveraging advanced type systems to enforce memory safety and prevent common errors that can lead to exploits.
For example, Rust’s ownership and borrowing system, combined with its strong static typing, enables the compiler to detect memory-related errors, significantly reducing the risk of vulnerabilities.
Improved Memory Management
Modern programming languages are increasingly adopting advanced memory management techniques to enhance security. These systems aim to prevent memory-related vulnerabilities, such as buffer overflows and use-after-free errors. Languages like Rust, with its unique ownership and borrowing system, exemplify this approach. This system enables the compiler to enforce strict rules about memory usage, significantly reducing the likelihood of such critical vulnerabilities.
The ability to detect memory safety issues during compilation rather than at runtime is a key benefit.
Formal Verification and Security Analysis
Formal verification and security analysis techniques are becoming more integrated into the development process. Tools and techniques are being developed to allow developers to rigorously analyze their code for potential security flaws. This approach, when combined with static analysis, can significantly improve the overall security posture of applications. For example, tools can be used to automatically check for vulnerabilities like SQL injection or cross-site scripting, providing developers with immediate feedback and reducing the risk of these common attack vectors.
Integration of Security Best Practices
Languages are starting to incorporate best practices for secure coding directly into their design. This approach allows developers to adhere to established security principles without having to rely solely on external libraries or frameworks. Languages are beginning to include features that encourage defensive programming practices, thereby promoting secure coding habits from the outset. This paradigm shift will help developers write more secure code by default.
Practical Application and Examples
Modern applications often demand robust security measures, and the choice of programming language significantly impacts their implementation. This section explores how different languages address security concerns in a practical context, showcasing the advantages and disadvantages of various approaches. Different languages prioritize different security features, leading to varying degrees of protection against common threats.
Hypothetical Application Scenario, Most secure programming languages 2025
Consider a hypothetical online banking application. This application requires secure handling of user credentials, transaction data, and preventing unauthorized access. Security vulnerabilities can lead to significant financial losses and reputational damage. Different languages will employ different techniques to address these security challenges.
Security-Sensitive Task Performance Comparison
| Programming Language | Authentication | Data Validation | Authorization | Performance (Estimated) |
|---|---|---|---|---|
| Rust | Strong, built-in features | Comprehensive, compile-time checks | Fine-grained control | High |
| Go | Robust libraries | Type safety, runtime checks | Well-defined access controls | High |
| Java | Strong security frameworks | Extensive validation libraries | Role-based access control | Medium |
| Python | Libraries for authentication | Validation with frameworks | Access control mechanisms | Moderate |
The table illustrates a simplified comparison of performance. Factors such as specific libraries used, code implementation, and hardware influence the actual performance figures.
Real-World Vulnerability Mitigation
SQL injection attacks are a common vulnerability. In Python, parameterized queries can prevent such attacks by separating the data from the query structure. This contrasts with direct string concatenation, which leaves the application vulnerable. Similarly, in languages like Java, the use of prepared statements mitigates the risk of injection attacks. Robust input validation is crucial in all languages.
Secure Libraries and Frameworks
Secure libraries and frameworks play a crucial role in application security. Rust’s standard library emphasizes memory safety and prevents common vulnerabilities. Go’s standard library includes secure cryptographic functions, simplifying the implementation of secure protocols. Java leverages frameworks like Spring Security for comprehensive authentication and authorization. Python utilizes libraries like Flask and Django with built-in security features for web applications.
Security Implications of Language Choice
Choosing a language with inherent security features, like Rust, often leads to more secure applications due to its compile-time checks and memory safety. Languages lacking compile-time checks may require more rigorous code reviews and runtime checks, leading to increased development effort and potentially slower performance. Security considerations should be central to the language selection process, with a clear understanding of the specific security requirements of the application.
Language Ecosystem and Support

Source: healsecurity.com
The strength of a programming language extends beyond its core syntax. A robust ecosystem encompassing libraries, frameworks, and community support significantly impacts its usability and security. Active communities often contribute to security-focused tools and resources, fostering a proactive approach to vulnerabilities. This section explores the varying levels of ecosystem support for secure programming in several prominent languages.
Ecosystem Strengths and Community Support
Different programming languages boast varying degrees of community engagement and support for security best practices. Languages with strong communities tend to have more readily available resources, tools, and security audits. This can translate to quicker identification and patching of vulnerabilities, ultimately enhancing overall security. Conversely, languages with smaller or less active communities may face challenges in accessing such resources.
Available Tools and Resources for Secure Coding
Numerous tools and resources aid developers in writing secure code within each language. Static analysis tools, for example, can identify potential vulnerabilities in the codebase before deployment. These tools, coupled with established coding guidelines and secure coding practices, are essential for minimizing risks. Dynamic analysis tools complement static analysis by identifying vulnerabilities during runtime. Libraries and frameworks frequently provide built-in security features, simplifying the development process while reducing security risks.
Security Audits and Code Analysis Tools
Security audits and code analysis tools play a crucial role in ensuring code quality and identifying potential vulnerabilities. Tools such as SonarQube, OWASP ZAP, and others provide automated assessments, helping developers pinpoint potential security flaws. Manual audits, performed by experienced security professionals, can complement automated tools, offering a more comprehensive review of the codebase. The use of these tools is crucial for identifying weaknesses that might otherwise be missed.
Security Resources for Each Language
Access to comprehensive documentation, security guidelines, and community forums is essential for developers. Each language typically possesses a range of security-focused resources, ranging from official documentation to external repositories of security best practices. These resources offer valuable insights and practical guidance for developers seeking to enhance the security of their applications.
Community Support and Resources Overview
This table summarizes the community support and available resources for selected programming languages, highlighting their strengths and weaknesses in the realm of security.
| Language | Community Support | Security Tools/Resources | Code Analysis Tools |
|---|---|---|---|
| Python | Large, active community with extensive libraries and frameworks. | Numerous security libraries (e.g., cryptography), OWASP ZAP integration. | Pylint, Bandit, and others. |
| Java | Very large and mature community with strong industry presence. | Extensive security libraries (e.g., Javax Cryptography), numerous security audit tools. | FindBugs, Checkstyle, and others. |
| C++ | Large but potentially less focused on security-specific tools compared to Python or Java. | Libraries like OpenSSL, but requires careful handling. | Cppcheck, Coverity, and others. |
| Go | Growing community with increasing security-focused resources. | Built-in security features and strong standard library. | GoSec, Go vet, and others. |
| Rust | Actively developing community with a focus on memory safety and security. | Built-in safety features, extensive documentation. | Miri, Clippy, and others. |
Outcome Summary: Most Secure Programming Languages 2025
In conclusion, the landscape of secure programming languages is constantly evolving, with languages like Rust pushing the boundaries of security through innovative features. The choices made today will shape the security of software for years to come. By understanding the key factors, comparing top contenders, and exploring emerging trends, developers can build more secure and resilient applications. This exploration provides a crucial framework for navigating the complexities of secure programming in 2025 and beyond.







Post Comment